SAML Authentication adds an extra layer of security to the password reset and account unlock process. If your organization already has SAML-based identity provider (IdP) applications such as OneLogin or Okta, it makes sense to use SAML Authentication as a method to verify users' identities. When SAML Authentication is enabled, users are redirected to their IdP login URL for authentication during password self-service operations. After successful authentication, users are routed back to the ADSelfService Plus portal where they can reset their password or unlock their account. To use SAML Authentication, end users do not have to enroll with ADSelfService Plus.
Configuration of SAML authentication must be done in two places:
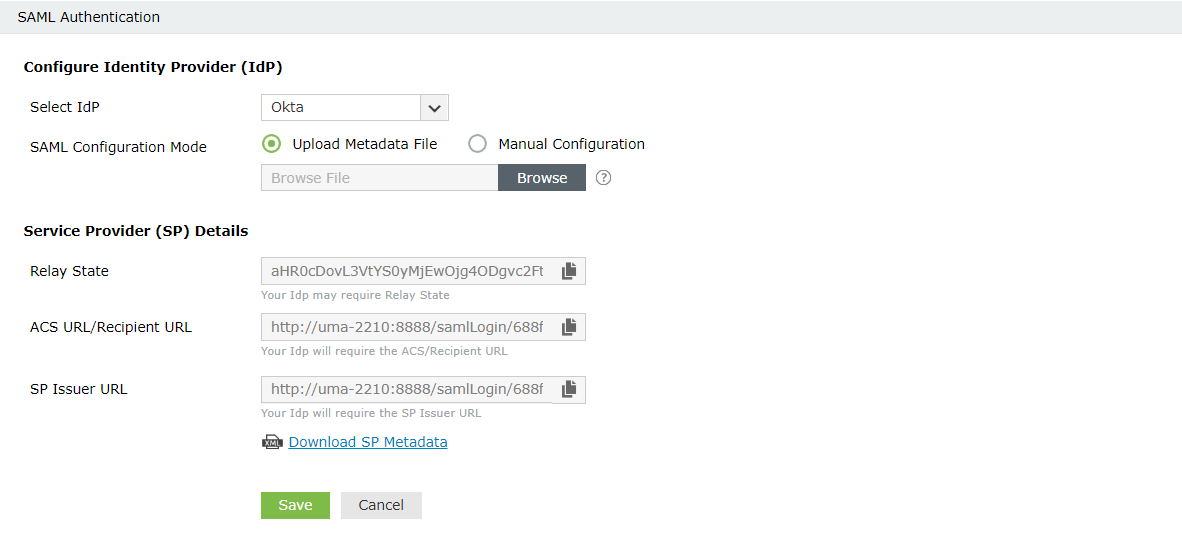
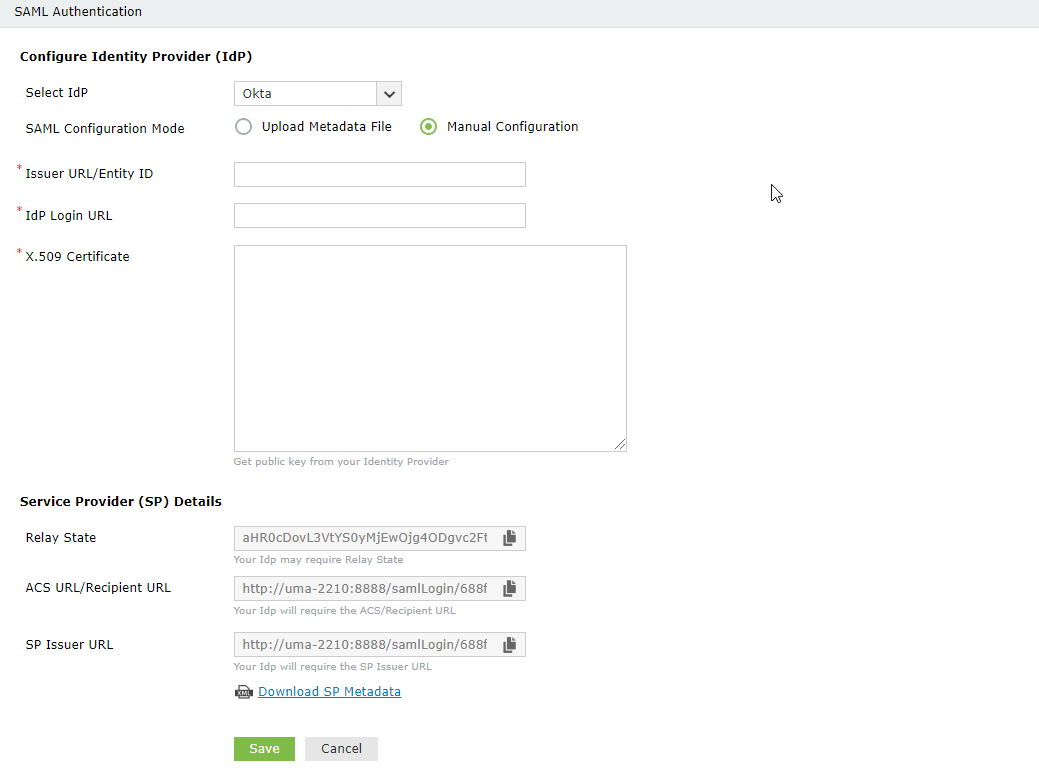
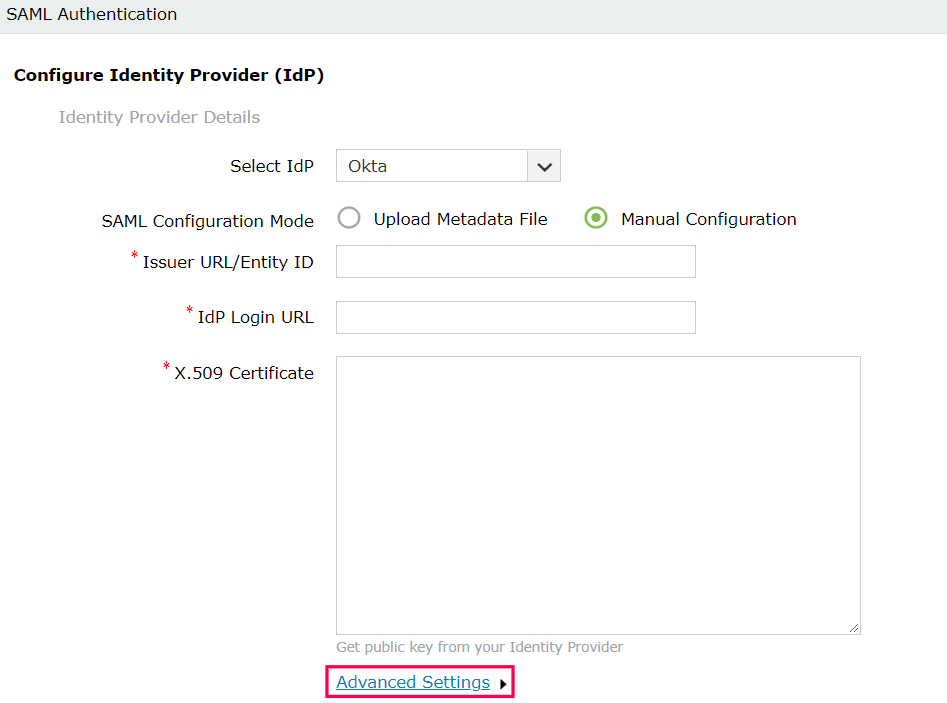
Here, the IdP is the SAML-based identity provider application such as OneLogin or Okta. The SP is ADSelfService Plus.
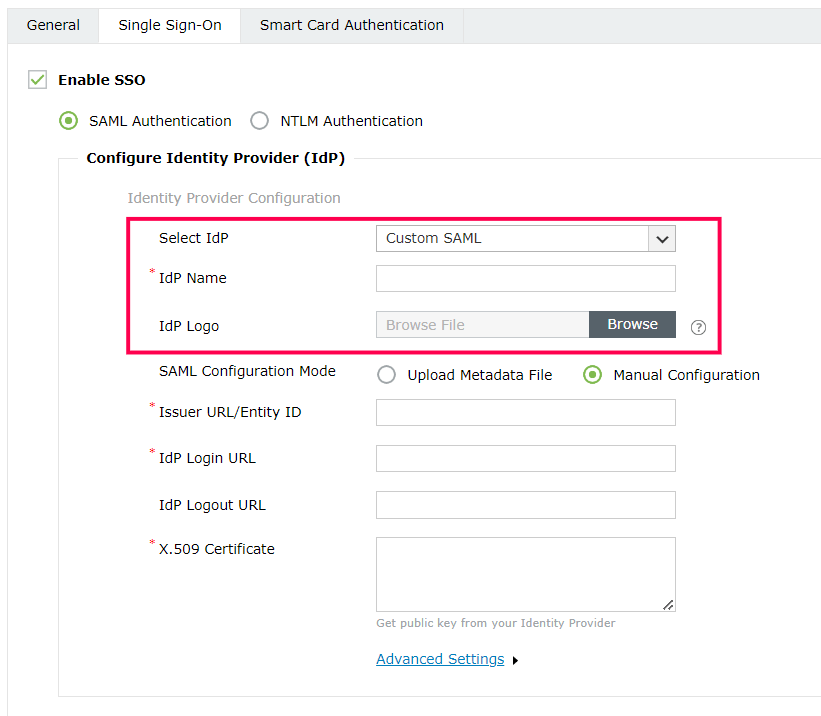
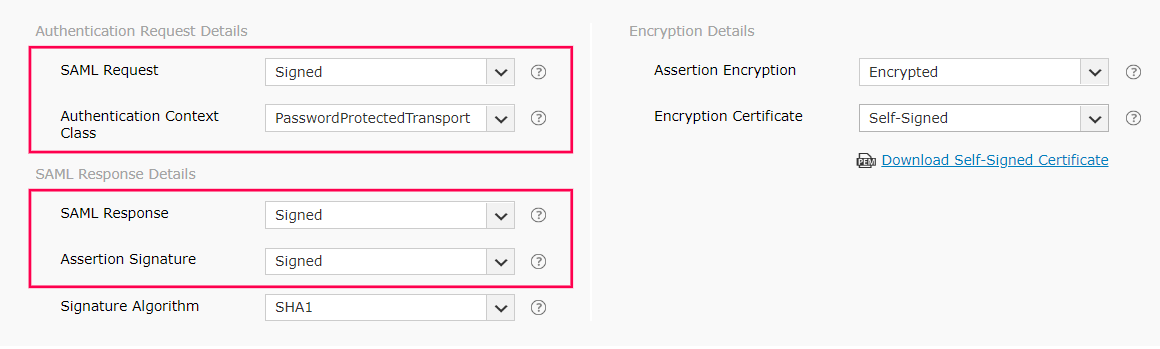
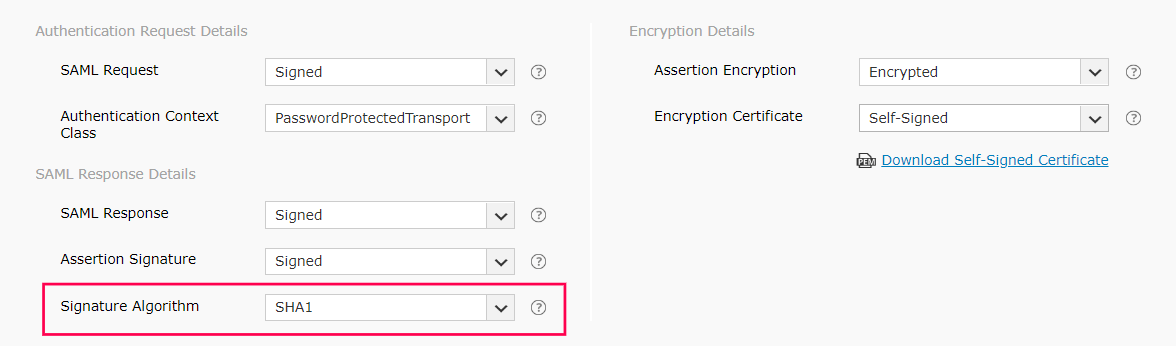
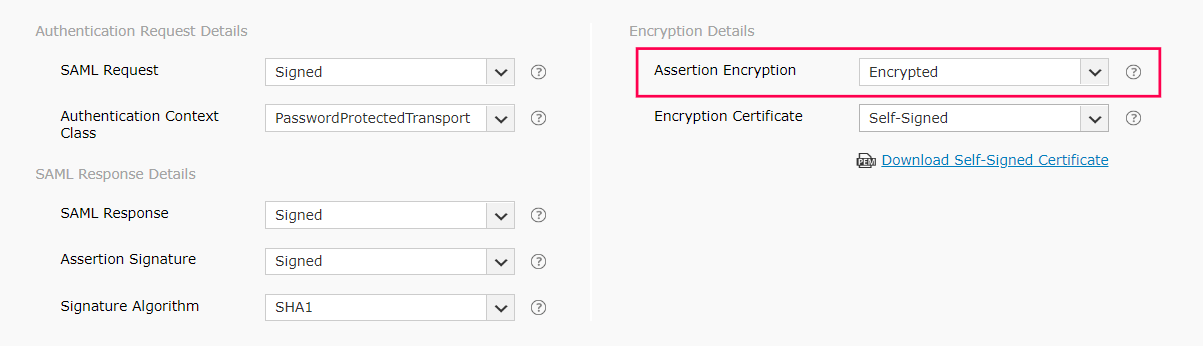
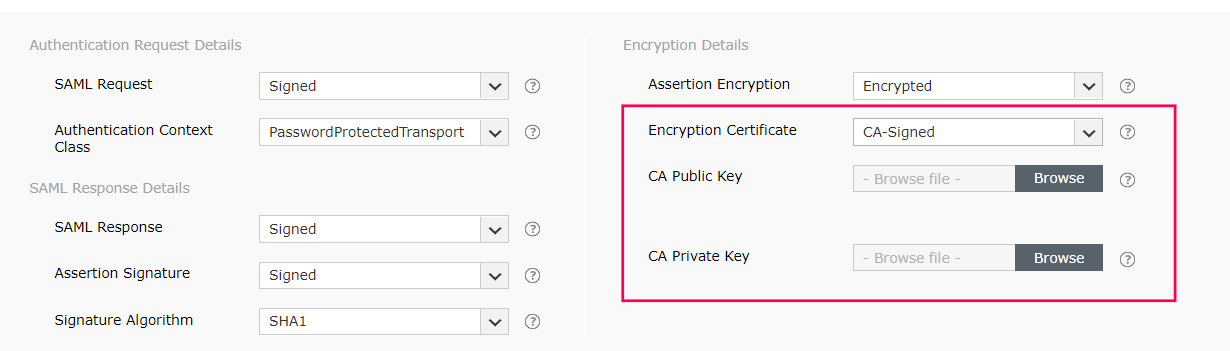
In General Settings, enter the SAML application name (Example: SelfService MFA) in the App name field. Upload a logo for the application if needed, then click Next.
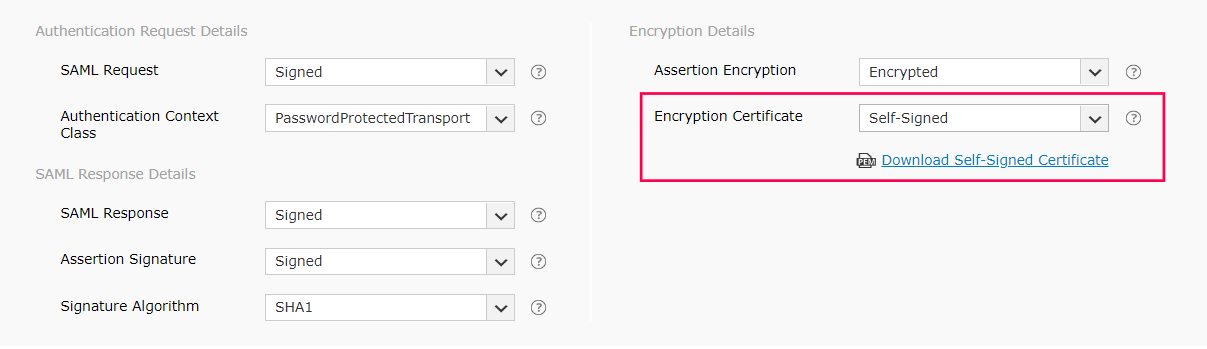
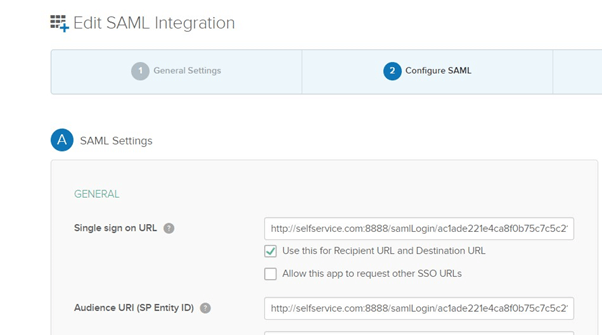
In Configure SAML, enter the ACS URL/Recipient URL into the Single sign on URL and Audience URI (SP Entity ID) fields.
ACS URL/Recipient URL: Log into ADSelfService Plus web console with admin credentials. Navigate to Configuration tab → Multi-factor Authentication → SAML authentication → ACS URL/Recipient URL. Copy the ACS URL/Recipient URL.
Click Next.
In Feedback, select an appropriate response and then click Finish.
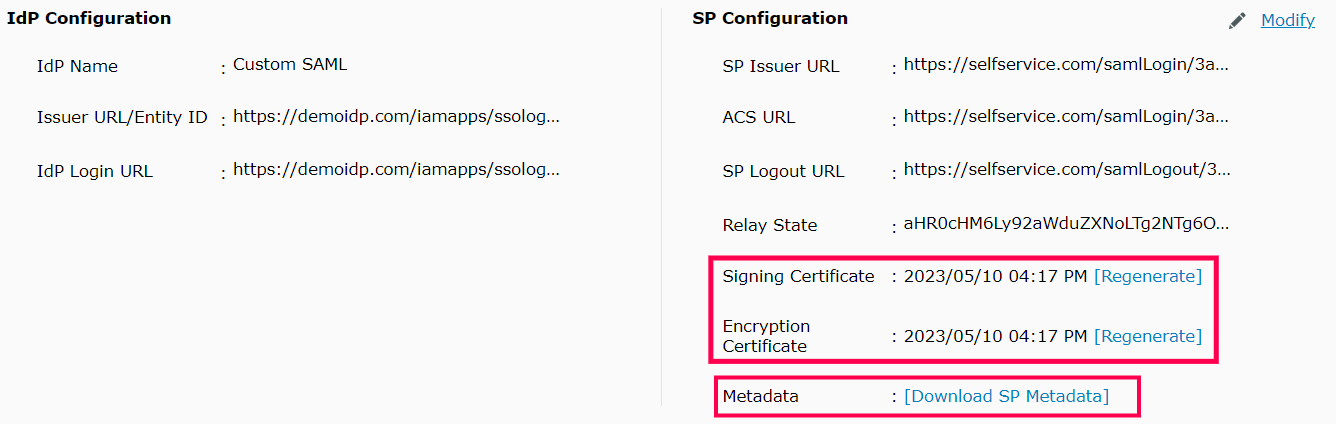
The Sign on tab of the newly created application appears. Download the metadata file by clicking the Identity Provider metadata link. You will need this file while configuring SAML authentication in ADSelfService Plus. So, save this file and keep it safe. Rename the downloaded metadata file as 'metadata_okta.xml'.
Click on the Assignments tab and navigate to Assign. Select Assign to People or Assign to Groups based on your requirement. After selecting an option, click the Save and Go Back button.
Click Done.
Find SAML in the Find Applications section. Select SAML Test Connector (IdP) from the search result.
Under the Configuration tab, enter the ACS URL/Recipient URL into the ACS (Consumer) URL Validator, ACS (Consumer) URL, Recipient, and Audience fields.
In the MORE ACTIONS button on the top panel, select SAML Metadata to download the metadata file. You will need this file while configuring SAML authentication in ADSelfService Plus. So, save this file and keep it safe.
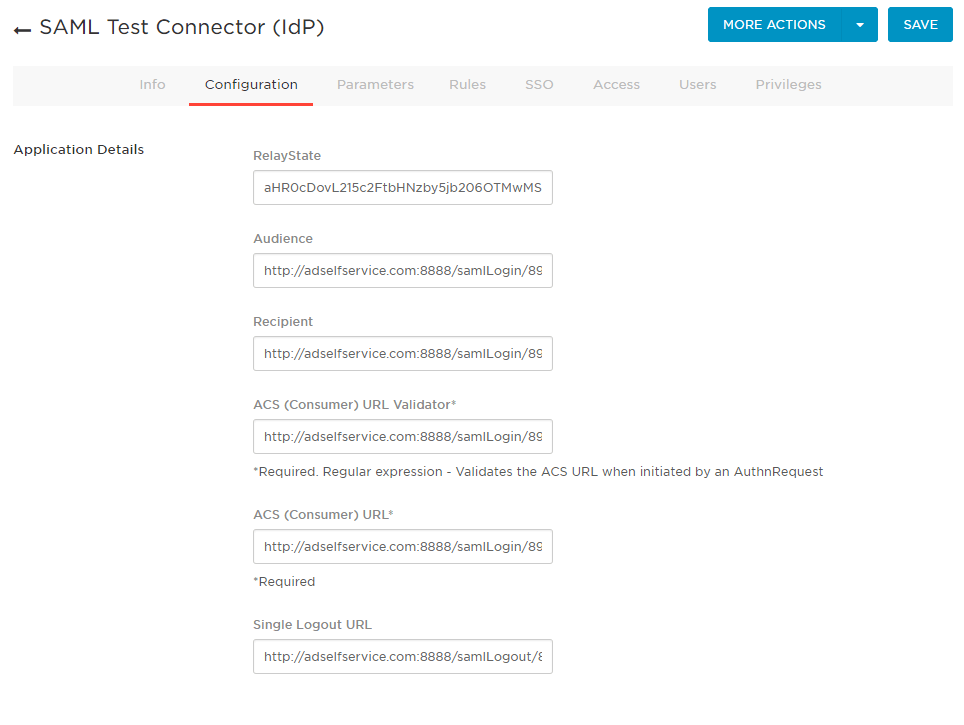
Click SAVE.
Prerequisites:
To configure AD FS for identity verification in ADSelfService Plus, you need the following components:
During configuration, you will need to add a Relying Party Trust and create claim rules.
A Relying Party Trust is created to establish the connection between two applications for authentication purposes by verifying claims. In this case, AD FS will trust the relying party (ADSelfService Plus) and authenticate users based on the claims generated.
Claims are generated from claim rules by applying certain conditions on them. A claim is an attribute that is used for identifying an entity, to establish access. For example, the Active Directory sAMAccountName.
Step 1: Adding a Relying Party Trust
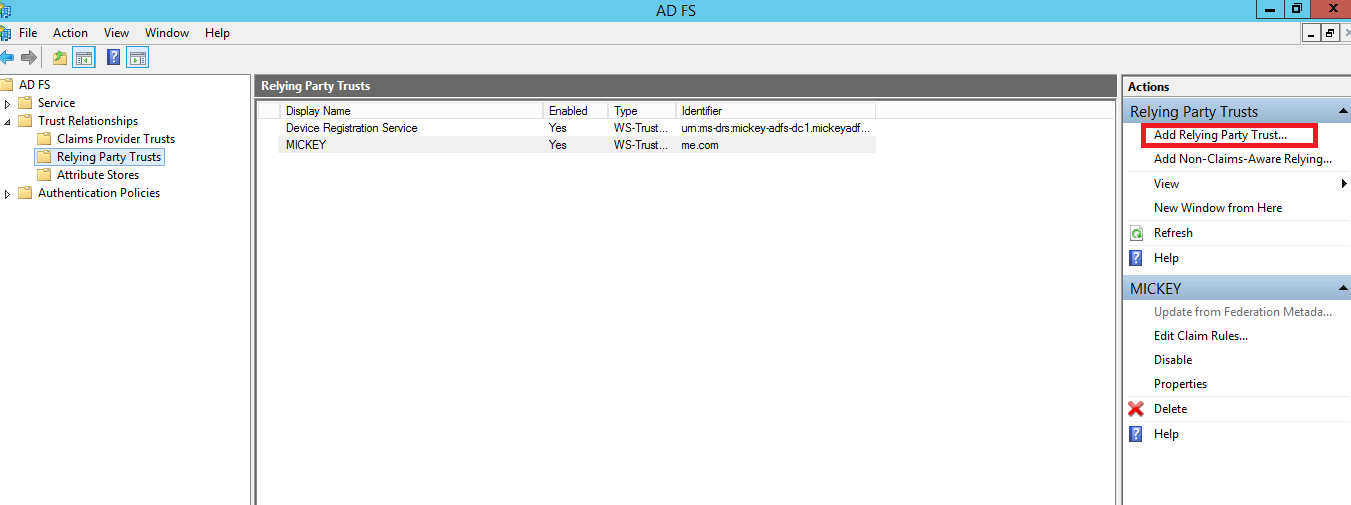
From the Actions sidebar, select Add Relying Party Trust. The Add Relying Party Trust Wizard opens.
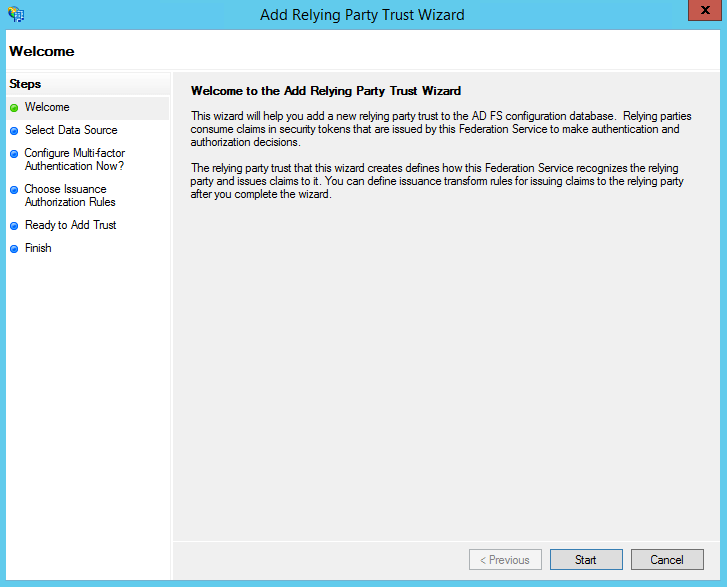
Click Start.
In the Select Data Source page, click on the Enter Data About the Party Manually option and click Next.
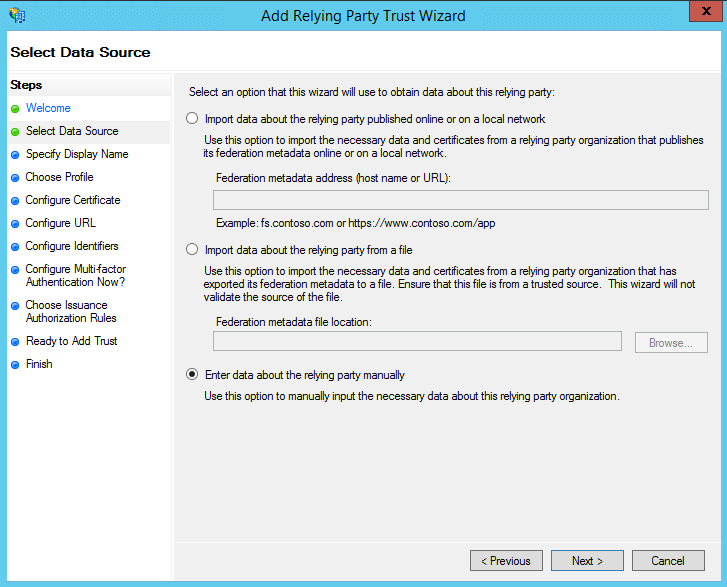
On the Specify Display Name screen, enter a display name of your choice, and additional notes if required. Click Next.
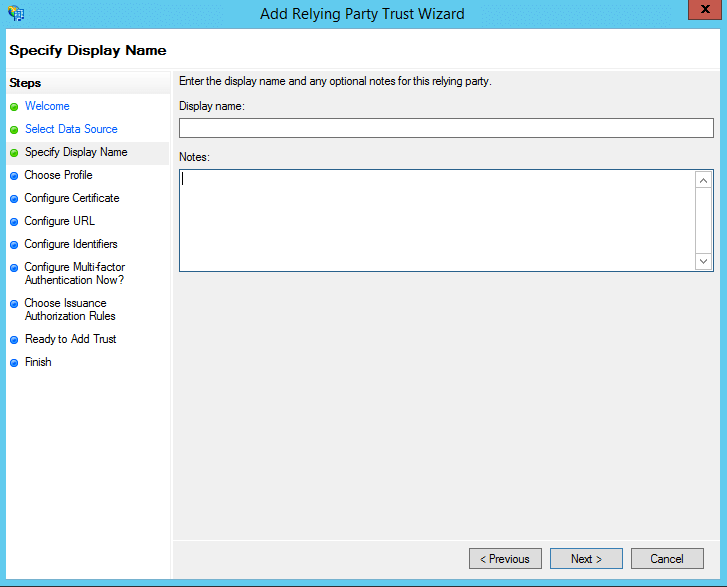
On the Choose Profile screen, click on the ADFS FS profile button. Click Next.
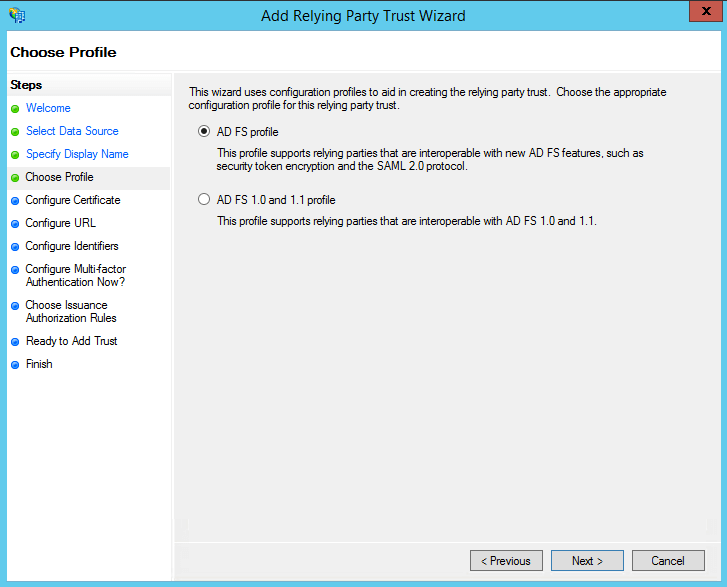
On the Configure Certificate screen, the default settings have already been applied. Click Next.
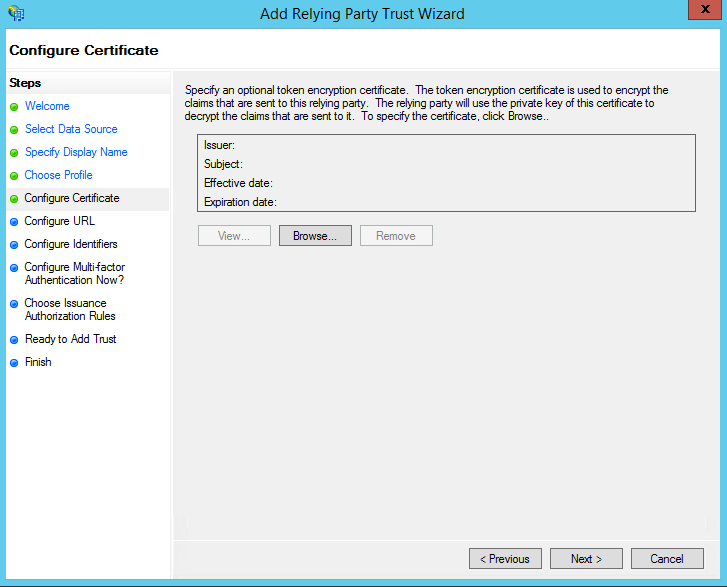
On the Configure URL screen, check the box labelled Enable Support for the SAML 2.0 WebSSO protocol. The Relying party SAML 2.0 SSO service URL will be the ACS URL of your ADSSP server. Note that there is no trailing slash at the end of the URL. For example:
https://selfservice.com/samlLogin/fdc0aa2a6d1801c525635ee0a71eb34196906b0f
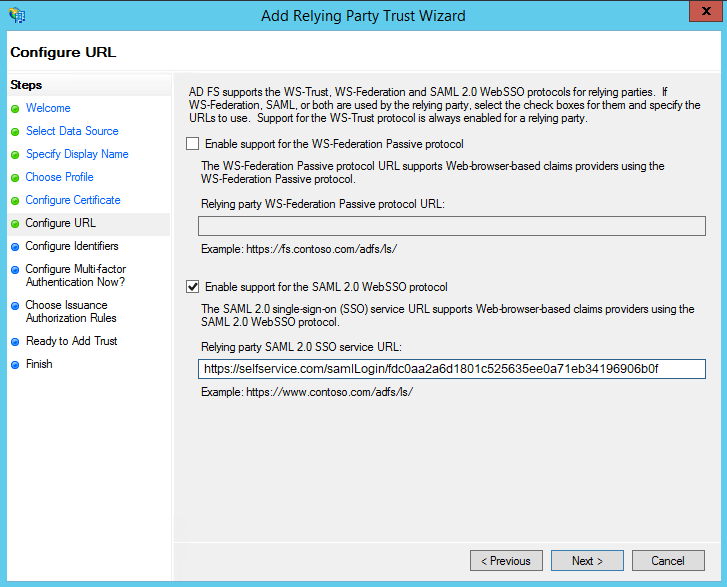
On the next screen, in the Relying party trust identifiers option, add SP Issuer URL (Ex: https://selfservice.com/samlLogin/fdc0aa2a6d1801c525635ee0a71eb34196906b0f)
On the next screen, you can choose to configure multi-factor authentication settings for the relying party trust. Click Next.
On the Choose Issuance Authorization Rules screen, you can choose to either Permit all users to access this relying party or Deny all users to access this relying party. Click Next.
The next two screens will display an overview of the settings you have configured. On the Finish screen, click Close to exit the wizard. If you have selected the Open the Edit Claim Rules dialog for this relying party trust when the wizard closes option, the Claim Rules editor will automatically open.
Step 2: Creating Claim Rules
Once you have configured the Relying Party Trust, you can create the claim rules using the Claim Rules Editor which opens by default when you finish creating the trust.
To create a new rule, click on Add Rule.
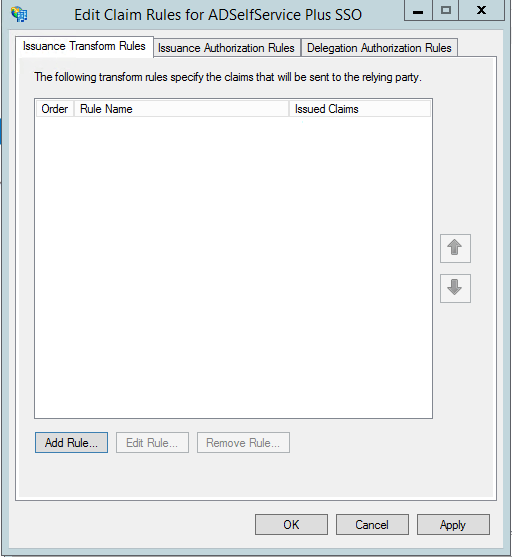
From the list of claim rule templates available, select Send LDAP Attributes as Claims. Click Next.
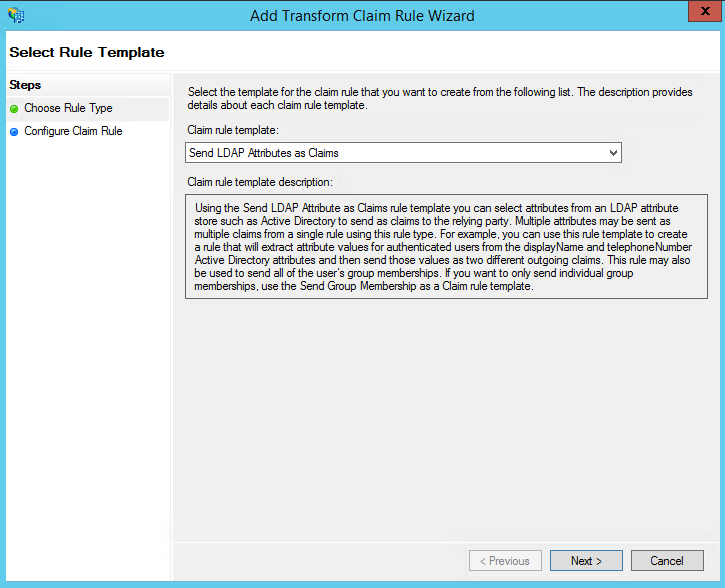
On the next page, provide a Claim rule name and select Active Directory as the attribute store.
From the LDAP Attribute column, select SAMAccountName.
From theOutgoing Claim Type column, select Name ID.
Click Finish to save the rule.
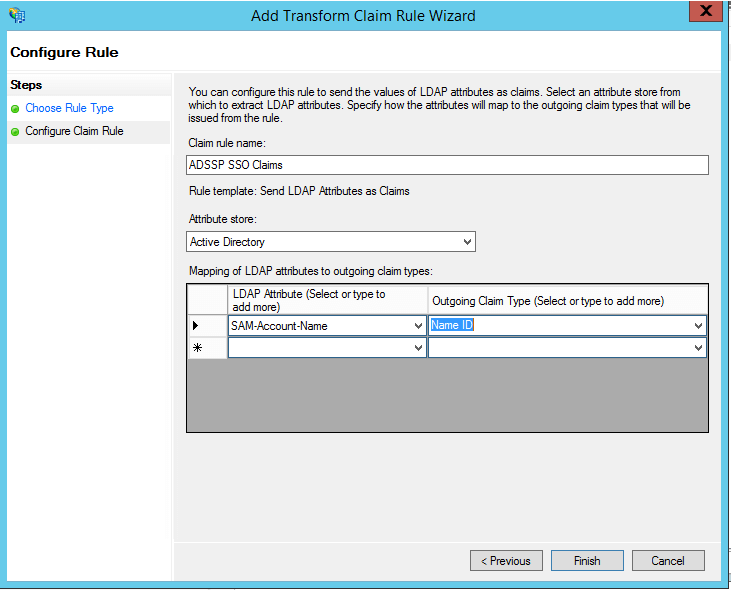
click Finish, you can view the rule that has been created.
After completing the AD FS configuration, download the metadata file by clicking on the Identity Provider metadata link. For example:
https://server_name/FederationMetadata/2007-06/FederationMetadata.xml.
You will need this file while configuring SAML authentication in ADSelfService Plus. So, save this file and keep it safe.
Navigate to the Relaying Party Trusts and find the rule you've created.
Right-click on the selected rule and click Properties.
In the window which opens, find the Endpoints tab and click Add SAML button.
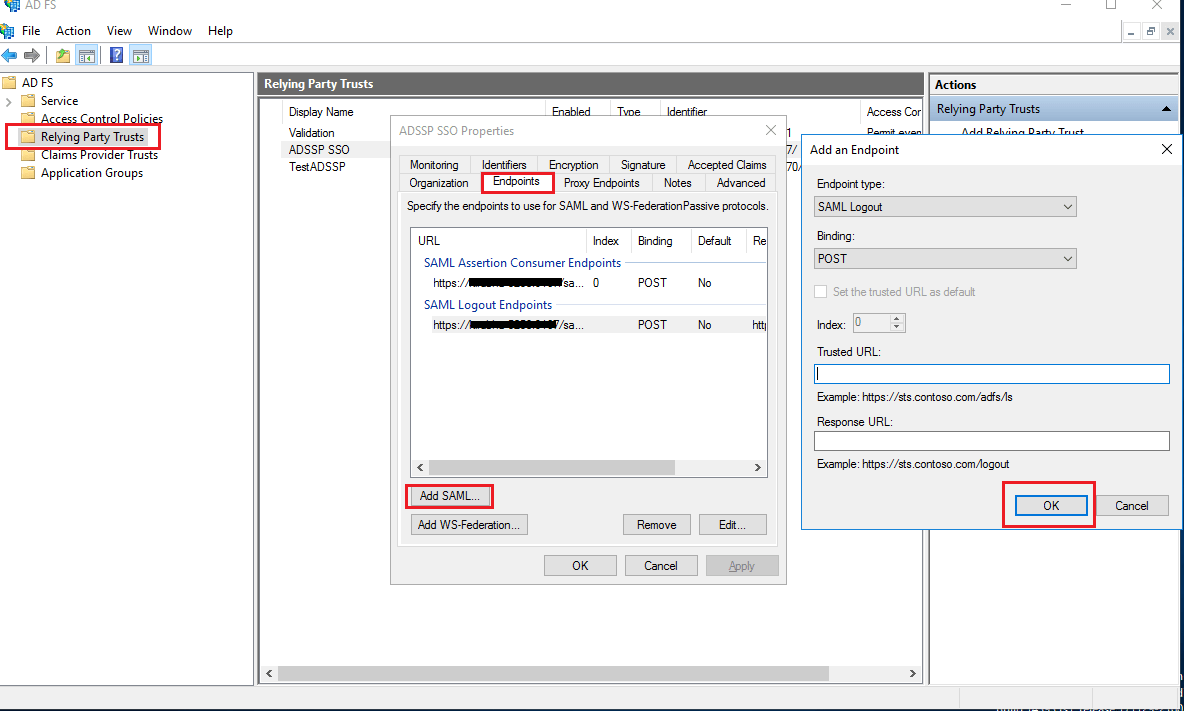
In the Trusted URL, paste the SP Logout URL copied from step 1 of prerequisites.
In the Signature tab, upload the X.509-certificate in PEM format from the step 4 of prerequisites.
Click OK.
Follow these steps to authenticate your ADSelfService Plus account through AD FS.
Prerequisite
Enable RelayState in AD FS.
For Windows Server 2012:
Navigate to the
%systemroot%\ADFS\Microsoft.IdentityServer.Servicehost.exe.config file in your AD FS server.
In the <microsoft.identityServer.web> section, enter the following code: <useRelayStateForIdpInitiatedSignOn enabled="true" />
Sample code:
<microsoft.identityServer.web>
…..
<useRelayStateForIdpInitiatedSignOn enabled="true" />
</microsoft.identityServer.web>
Restart the AD FS server.
For Windows Server 2016:
Open Powershell with administrative properties in your AD FS server.
Run the following command to enable IdP-initiated SSO:
Set-ADFSProperties -EnableIdPInitiatedSignonPage $true
Run the following code to enable RelayState:
Set-ADFSProperties -EnableRelayStateForIDPInitiatedSignon $true
Restart the ADFS server.
Steps to generate an IdP URL:
Log in to ADSelfService Plus web console with admin credentials.
Navigate to Admin tab → SSO Settings.
In the Service Provider Details section of SAML Authentication, copy the Relay State and the SP Issuer URL.
Open a word processor and enter the following command:
<IdP_URL_String>RelayState=RPID=<SP_Issuer_URL>&RelayState=<Relay State>
Give the word document a name, and save it. Encode the saved URL.
Sample code:
Once the code is encoded, it will look like the URL below:
https://example.com/adfs/ls/idpinitiatedsignon.aspx?RelayState=RPID%3Dhttps%253A%252F%252Fselfservice-0001%253A9267%252FsamlLogin%252F88d9537b8c5f7376fc78fdfb7591601e85aa8ebb%26RelayState%3DaHR0cHM6Ly9raXJ1YmhhLTUyNTg6OTI2Ny9zYW1sTG9naW4vTG9naW5BdXRo
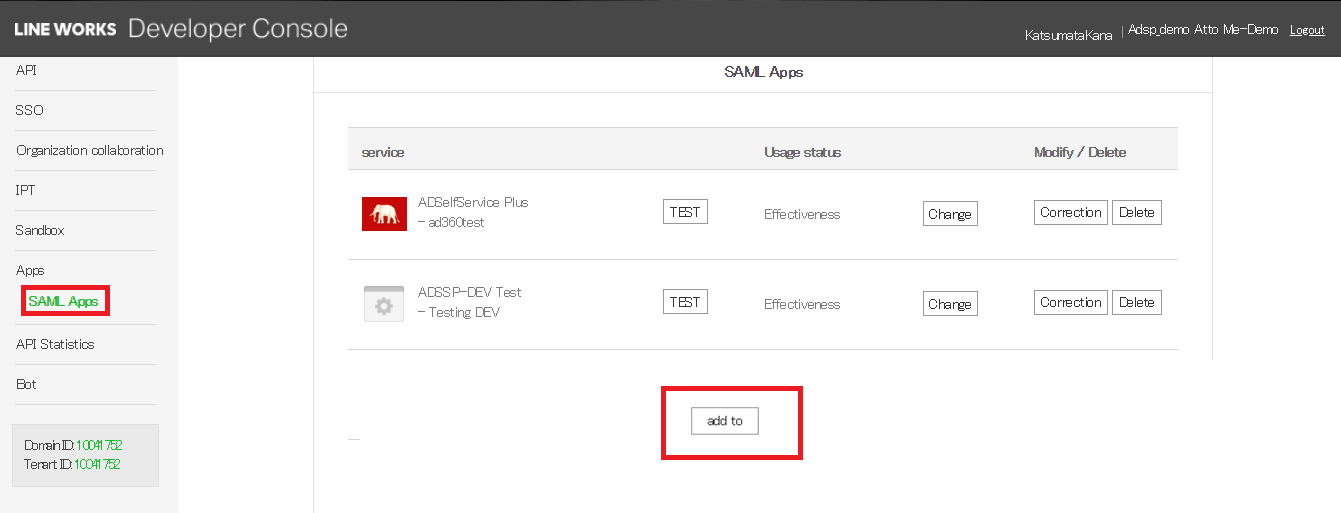
Log in to Line Works Developer console. Go to the Apps section > SAML Apps click add to button.
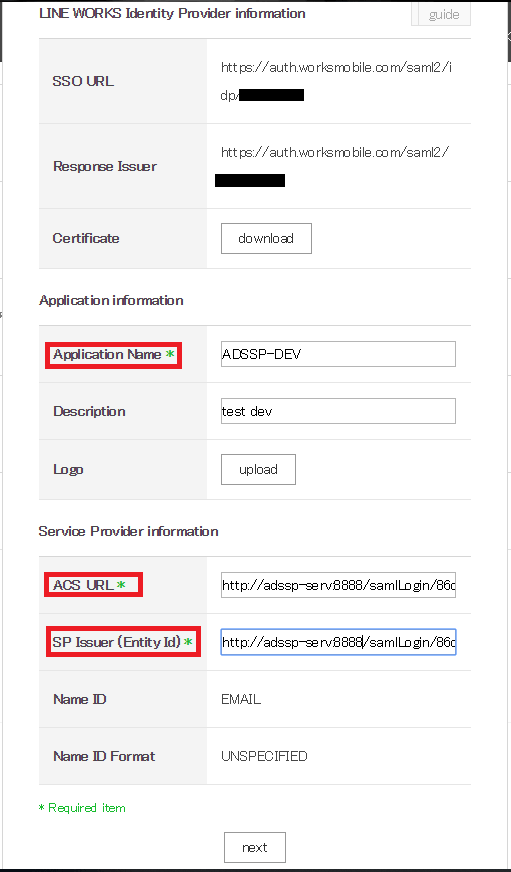
In the window that opens, provide an appropriate Application Name, Description, and Logo in the respective fields.
In the ACS URL field and the Issuer URL/Entity ID, enter the ACS URL/Recipient URL of ADSelfService Plus.
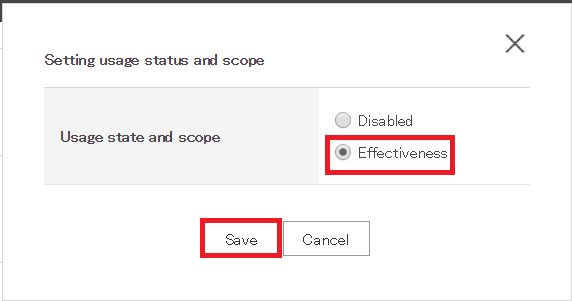
Go to SAML Apps section and find the application you have just created. Click the Change button and change the status to 'Effectiveness'. Click Save.
Copyright © 2023, ZOHO Corp. All Rights Reserved.