ADSelfService Plus MFA augments the traditional username and password-based authentication with an additional layer of authentication (e.g. biometric or a OTP) to verify a user's identity. MFA provides a high level of identity assurance for access requests.
You can enable MFA in ADSelfService Plus for the following events:
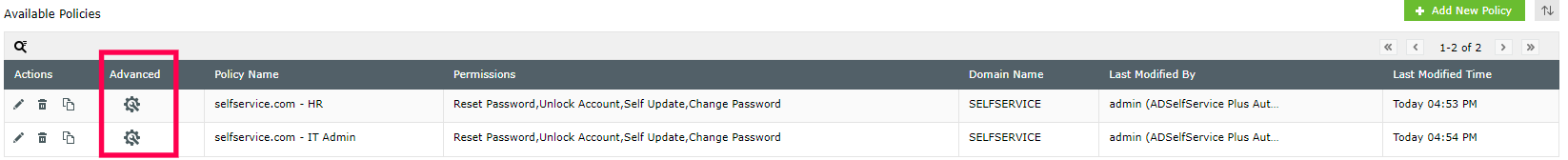
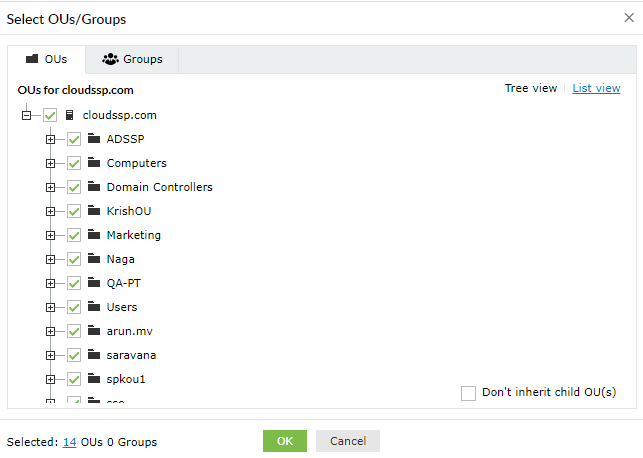
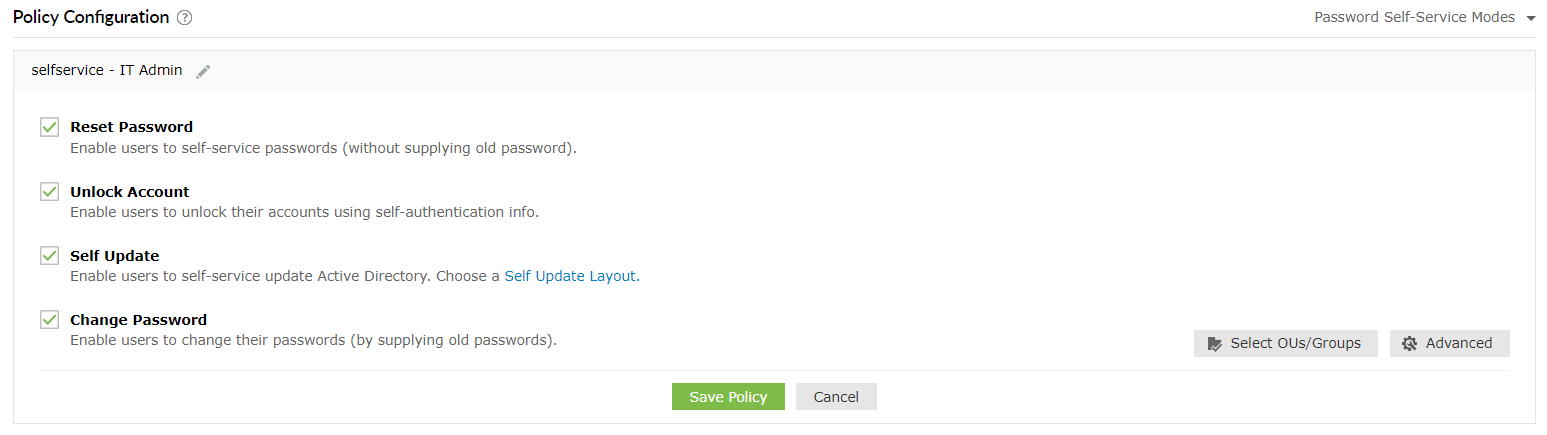
To enable MFA for these events:
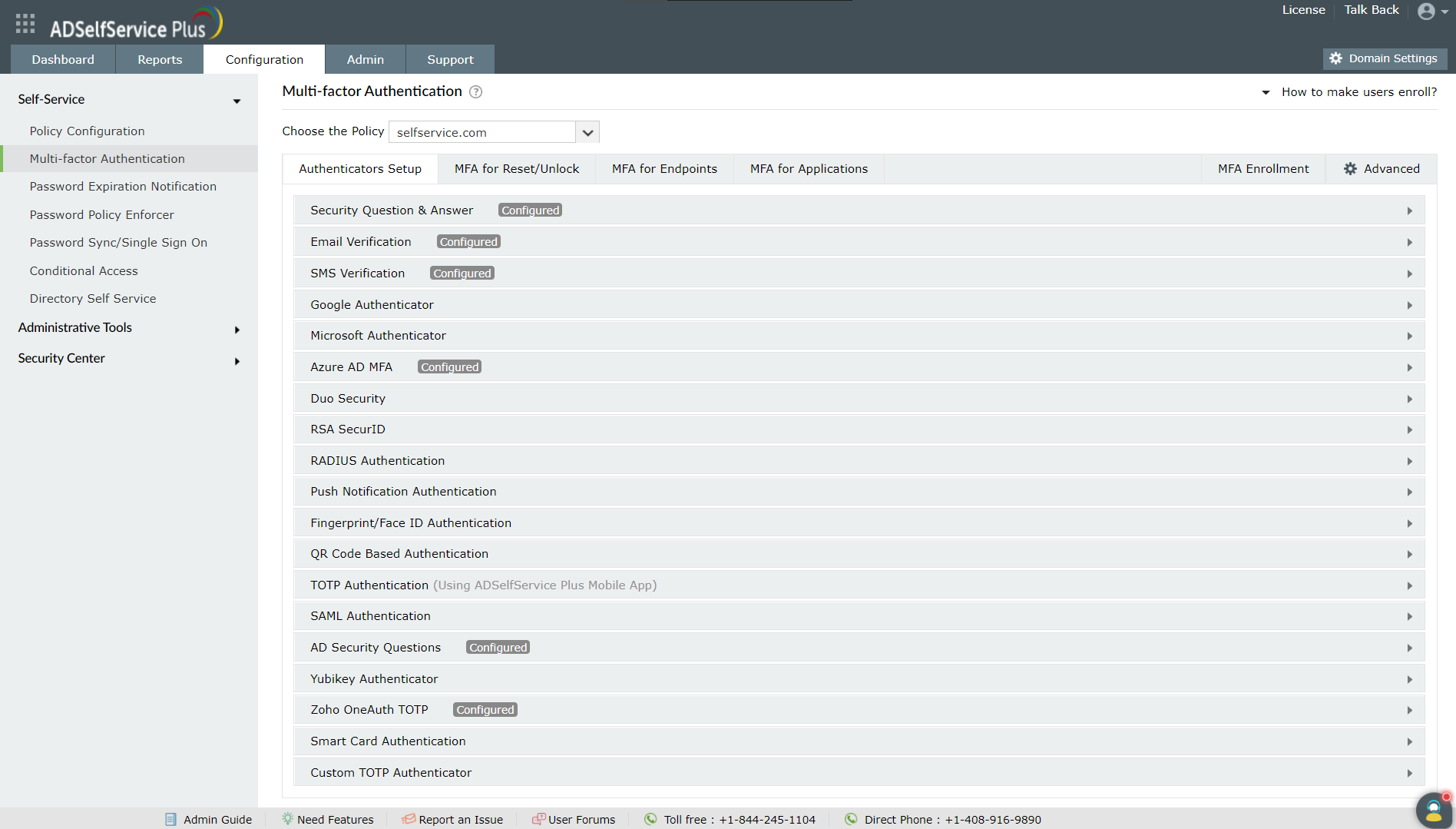
Refer to the Authenticators page for the list of supported authentication methods, and how to configure them.
Combined with Conditional Access, MFA for Endpoints can be enabled only for high-risk users, thus ensuring security without affecting user experience. Click here to learn more about Conditional Access.
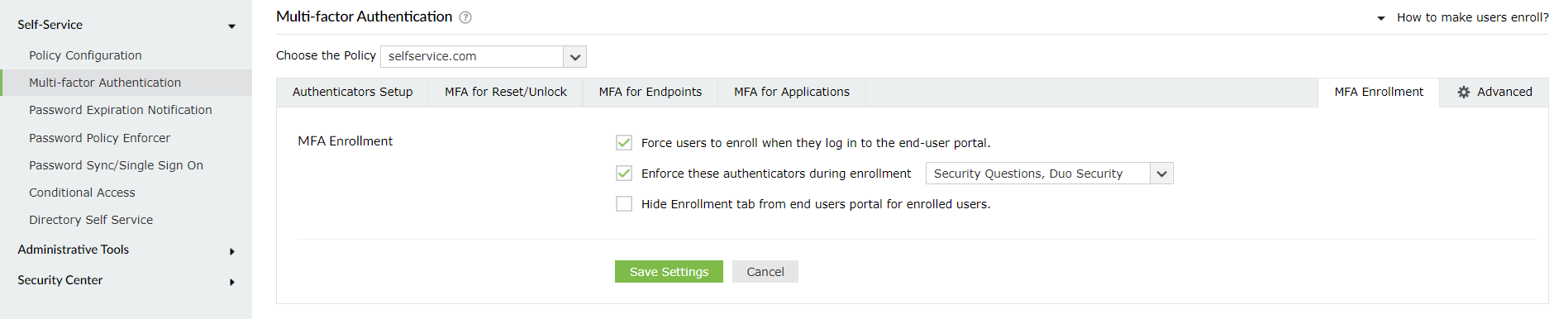
Users must enroll themselves by providing the necessary information, as per the enabled authentication methods, to be able to prove their identity. For example, if you have enabled Fingerprint Authentication, users must scan their fingerprint using the ADSelfService Plus mobile app, only after which, they will be able to use that method during password reset or endpoint logins.
To force users to enroll for specific authentication methods:
This table provides detailed information on each MFA type, including the supported authenticators and the settings and options available to improve the functionality and security of the authentication process.
| MFA type | Authentication methods supported | Passwordless login | Backup recovery codes | CAPTCHA |
|---|---|---|---|---|
| MFA for self-service actions | All the authenticators supported by ADSelfService Plus except for smart card authentication | Not applicable | Supported | Supported |
| MFA for Windows, macOS, and Linux logins | All the authenticators supported by ADSelfService Plus except for smart card authentication | Not applicable | Supported | Supported |
| Offline MFA for Windows logins. |
|
Not applicable | Not supported | Not supported |
| MFA for OWA and Exchange admin center | All the authenticators supported by ADSelfService Plus except for smart card authentication | Not applicable | Supported | Supported |
| MFA for RADIUS-based VPNs, RDP, and other endpoints |
|
Not applicable | Supported* (Backup codes can be used only for challenge-based authenticators) |
Not applicable |
| MFA for cloud applications | All the authenticators supported by ADSelfService Plus | Supported | Supported | Supported |
| MFA for ADSelfService Plus login | All the authenticators supported by ADSelfService Plus | Supported | Supported | Supported |
| MFA type | Can an idle time limit be set? | Can the browser or machine be trusted not to require MFA for a certain period? | Restrict user logins and self-service actions for unenrolled users: |
|---|---|---|---|
| MFA for self-service actions | Yes | No | Deny access to self-service actions when users are unenrolled. Partially enrolled users can be forced to enroll for the unenrolled authenticators and proceed with self-service actions. |
| MFA for Windows, macOS, and Linux logins | Yes | No | Deny or allow machine logins for unenrolled users, or enforce enrollment during login attempt. |
| MFA for OWA and Exchange admin center | Yes | No | Access to OWA and Exchange logins is denied for unenrolled users by default. |
| MFA for RADIUS-based VPNs, RDP, and other endpoints | Yes* (A session time limit is set to enforce users to complete authentication within the specified time) |
No | Deny or allow logins for unenrolled users. |
| MFA for cloud applications | Yes | Yes | Deny or allow cloud application logins for unenrolled users. |
| MFA for ADSelfService Plus login | Yes | Yes | Deny or allow ADSelfService Plus logins for unenrolled users. |
This table provides detailed information on the authenticators supported for MFA in the ADSelfService Plus mobile app and mobile browser portal along with provisions for authenticator enrollment in the two consoles.
| Authenticator | Mobile browser portal | Mobile app | |||
|---|---|---|---|---|---|
| Can users enroll in the authenticator in the mobile browser portal? | Is the authenticator supported for MFA for ADSelfService Plus logins? | Is the authenticator supported for MFA for self-service actions? | Can users enroll in the authenticator in the mobile app? | Is the authenticator supported for MFA for self-service actions? | |
| Security Question and Answer | Yes | Yes | Yes | Yes | Yes |
| Email Verification | Yes | Yes | Yes | Yes | Yes |
| SMS Verification | Yes | Yes | Yes | Yes | Yes |
| Google Authenticator | Yes | Yes | Yes | Yes | Yes |
| Microsoft Authenticator | Yes | Yes | Yes | Yes | Yes |
| Duo Security | Yes | Yes | Yes | Yes | Yes |
| Radius Authentication | No* | Yes | Yes | No* | Yes |
| Push Notification | No+ | No+ | No+ | Yes | Yes |
| QR Code Based Authentication | No+ | No+ | No+ | Yes | N/A |
| Fingerprint/Face ID Authentication | No+ | No+ | No+ | Yes | Yes |
| TOTP Authentication (Using ADSelfService Plus Mobile app) | No+ | No+ | No+ | Yes | N/A |
| AD Security Questions | No* | Yes | Yes | No* | Yes |
| Zoho OneAuth TOTP | No | Yes | Yes | Yes | Yes |
| Custom TOTP authenticator | Yes | Yes | Yes | Yes | Yes |
| Smart Card Authentication | No* | No | No | No* | No |
| SAML Authentication | No* | Yes | Yes | No* | Yes |
| YubiKey Authenticator | Yes | Yes | Yes | Yes | Yes |
| Azure AD MFA | No* | Yes | Yes | No* | Yes |
| RSA SecurID | No* | Yes | Yes | No* | Yes |
* - Users do not have to enroll for these methods because they are automatically enrolled upon logging in the first time.
+ - These authenticators are native to the mobile app and cannot be used in the mobile browser portal.
Copyright © 2023, ZOHO Corp. All Rights Reserved.