Configuring OpenID and OAuth SSO for Freshdesk
These steps show you how to configure the single sign-on (SSO) functionality using OpenID Connect and OAuth to Freshdesk from ManageEngine ADSelfService Plus.
- Do not terminate the session before the configuration is complete in both the identity provider and the service provider.
- Please enable HTTPS is the product to ensure proper functioning of single sign-on.
- Login to ADSelfService Plus as Administrator.
- Go to Configuration > Password Sync/ Single Sign On and click Add Application. Select Freshdesk from the list.
Note: You can also use the search bar, in the top-left, to search for the application.
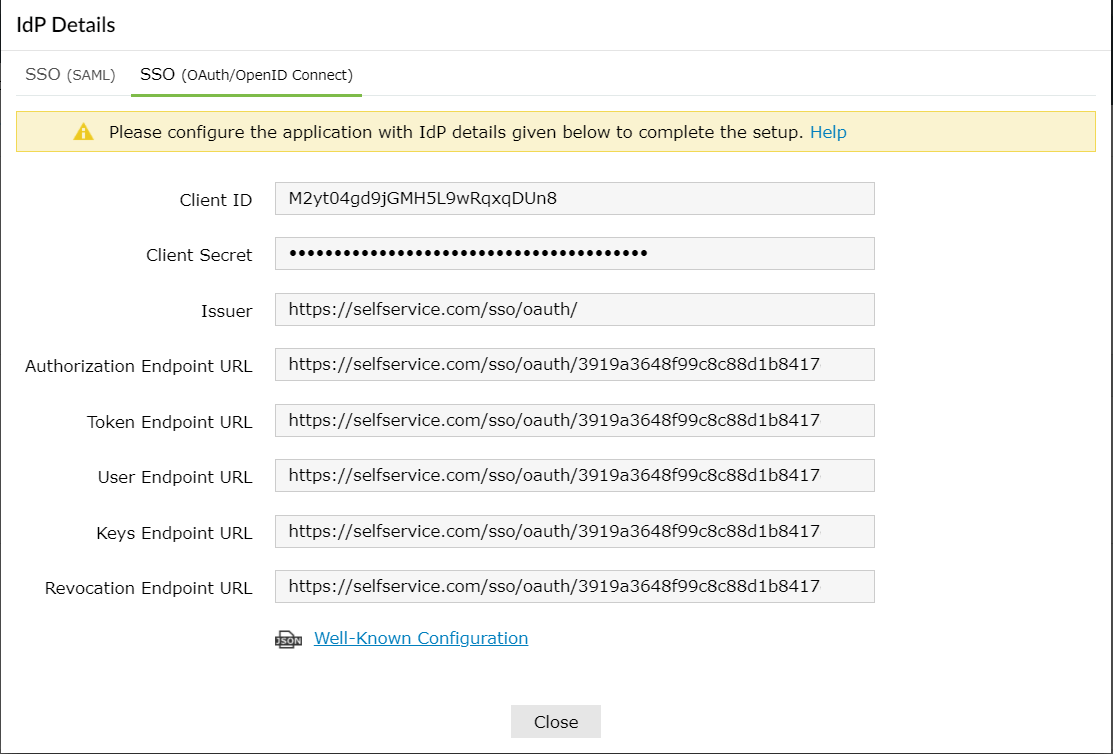
- Click on IdP Details and select the SSO (OAuth/OpenID Connect) tab.
- Copy Client ID, Client Secret, Authorization Endpoint URL, Token Endpoint URL, and User Endpoint URL.
Freshdesk (service provider) configuration steps
- Login to Freshdesk with admin credentials.
- Navigate to Security from the Admin tab.
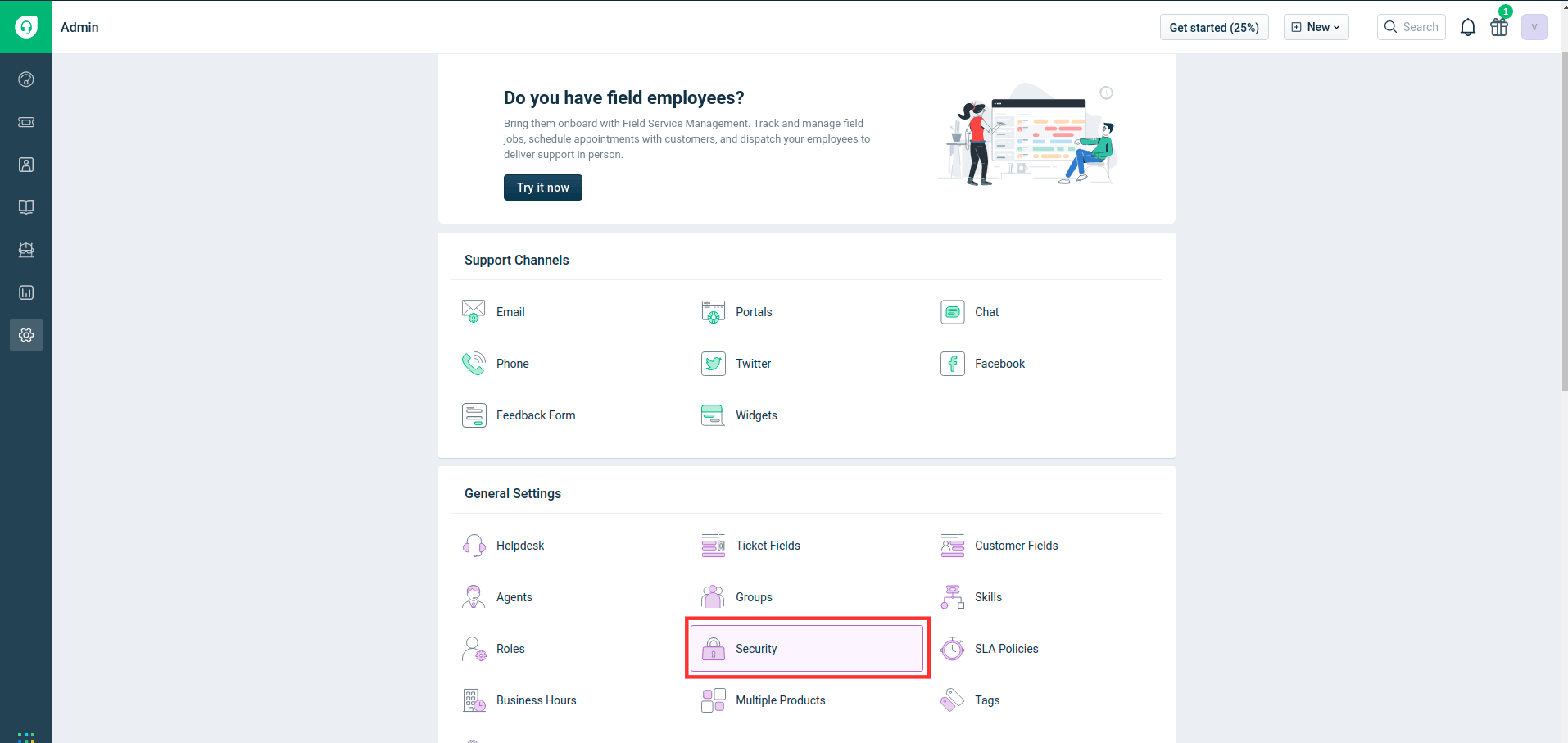
- In the Security page, under Login settings, click Edit Configuration within Freshworks SSO.
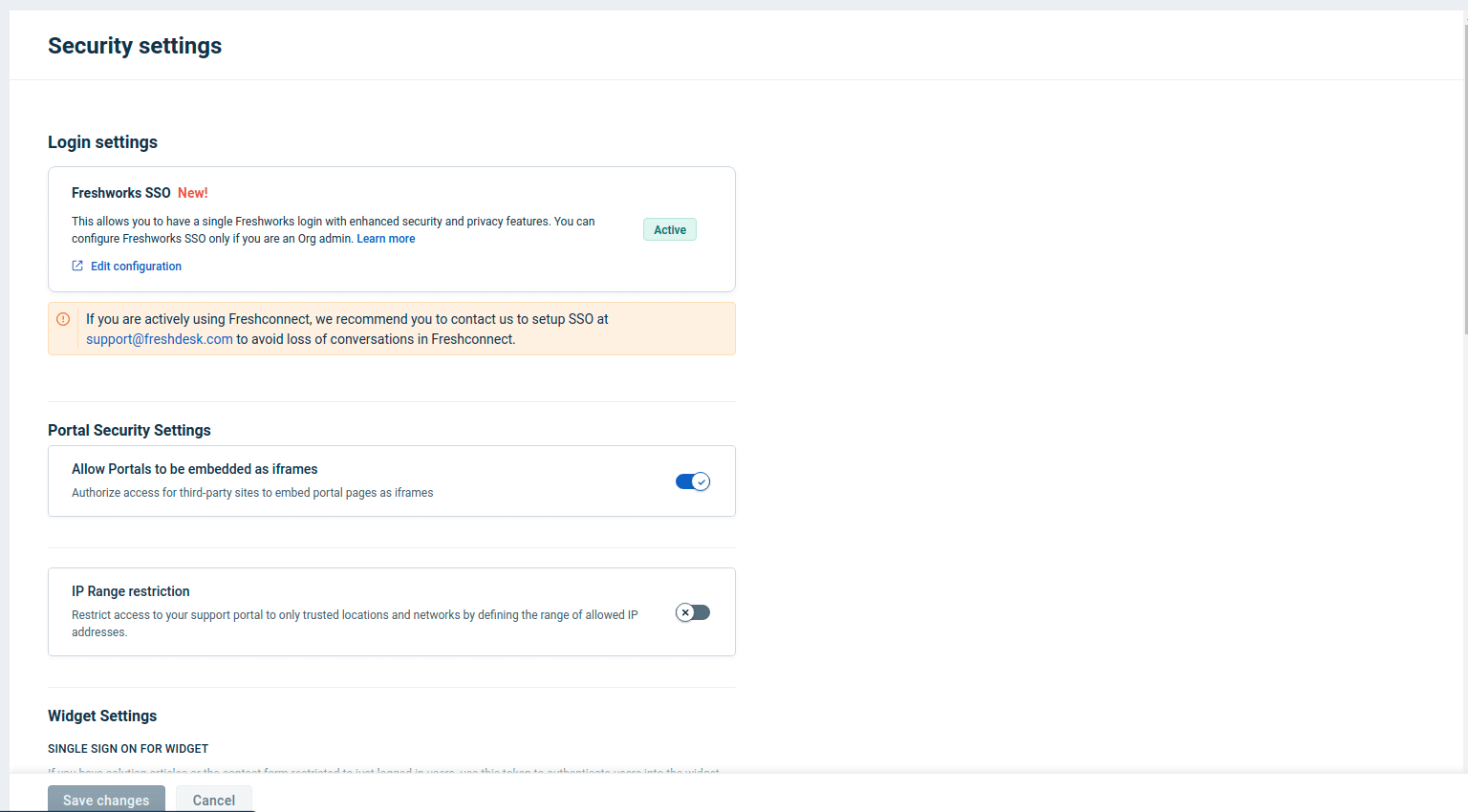
- In the page that appears, go to Security → Default Login Methods.
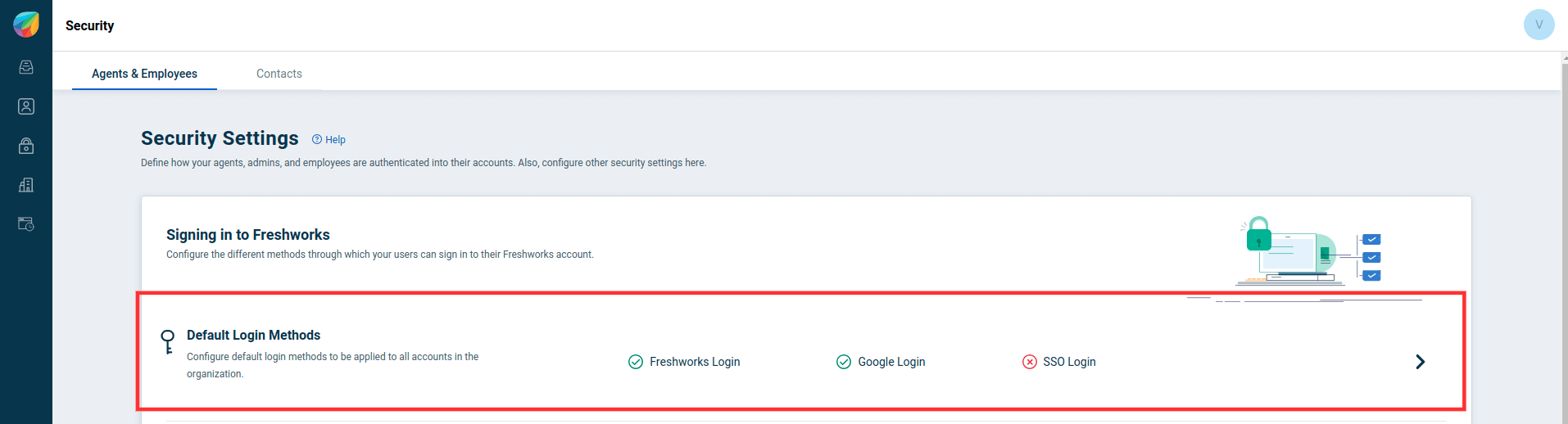
- Click on the toggle button next to SSO Login.
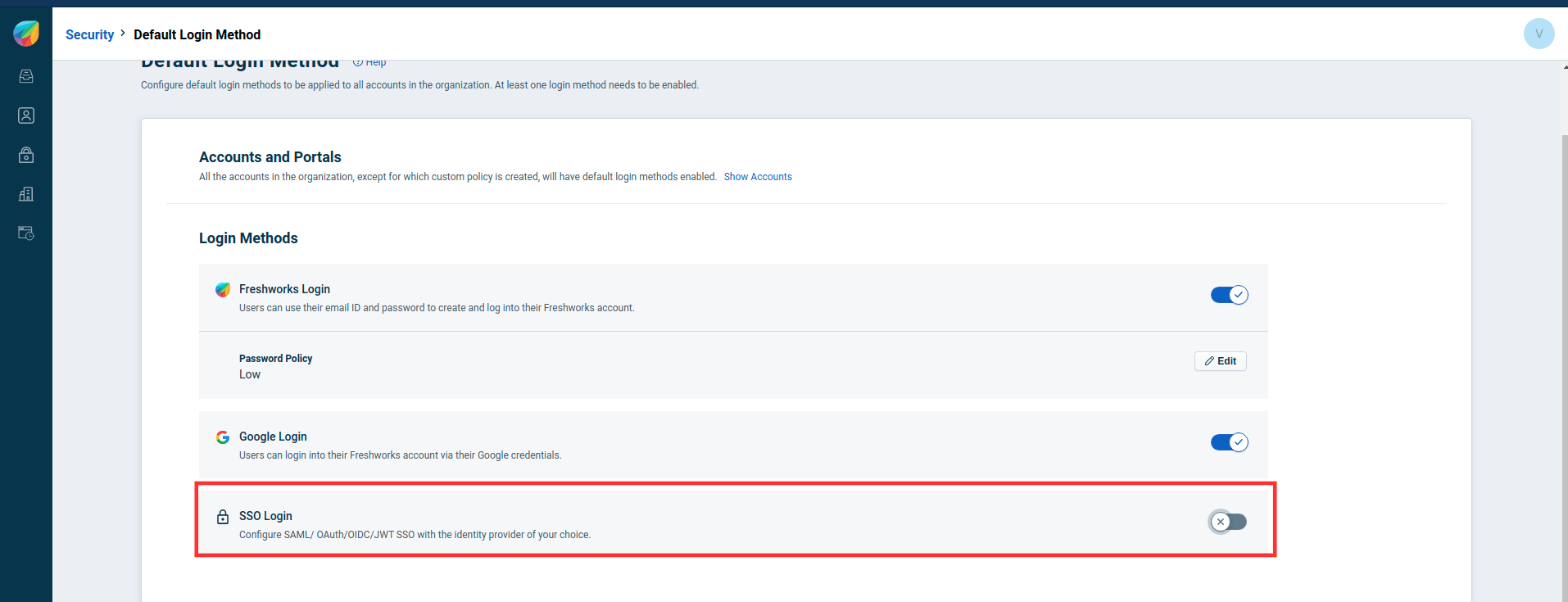
- Select OIDC or OAuth 2.0 under IdP of your choice, as per your preference.
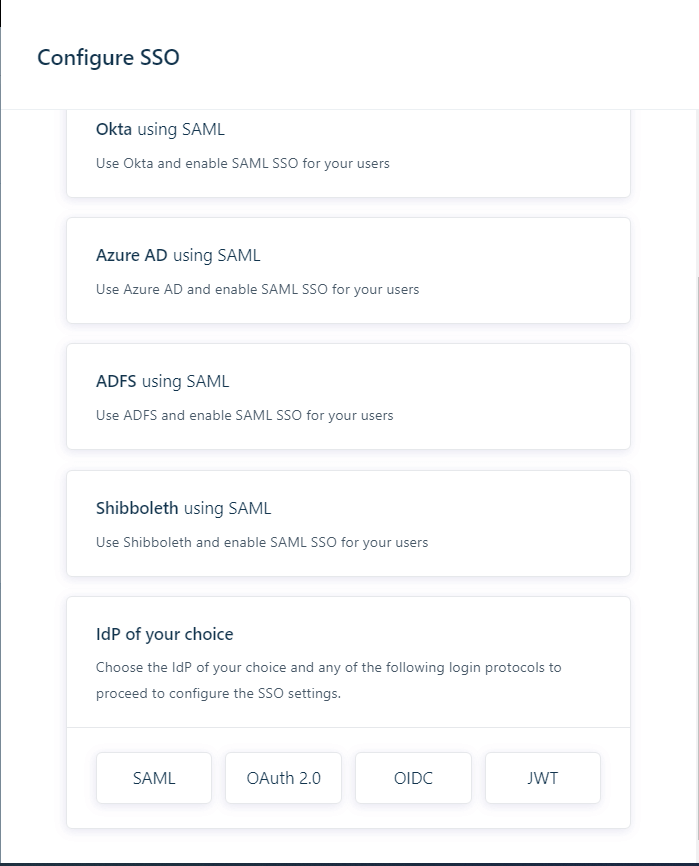
- For OIDC, fill the following fields, under Map information from IdP, with the corresponding details saved in step 4 of Prerequisites:
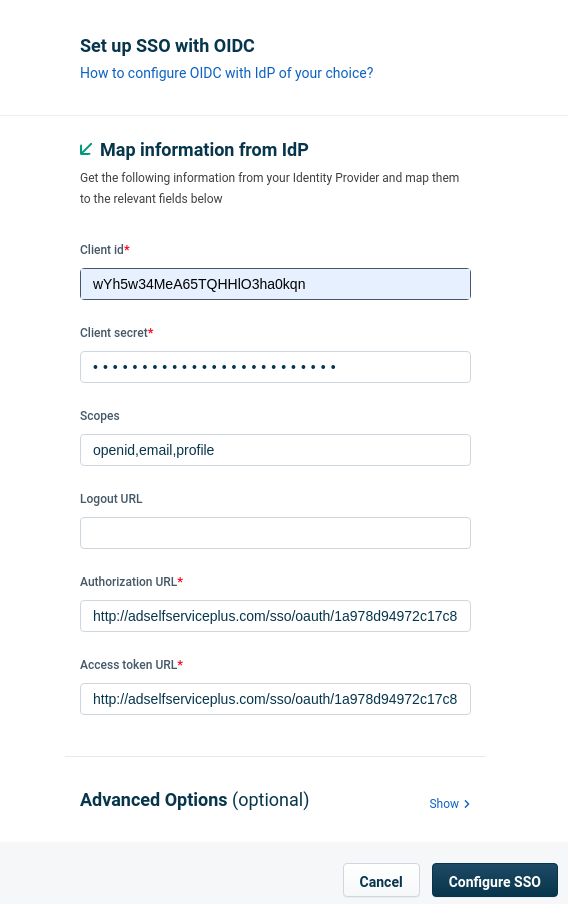
- Client id : Client ID
- Client Secret: Client Secret
- Select the Scopes to specify the level of access of the access tokens.
- Authorization URL: Authorization Endpoint URL
- Access token URL: Token Endpoint URL
- For OAuth 2.0, you will have to fill all the details in the previous two steps, plus the User info URL field with the User Endpoint value saved in step 4 of Prerequisites.
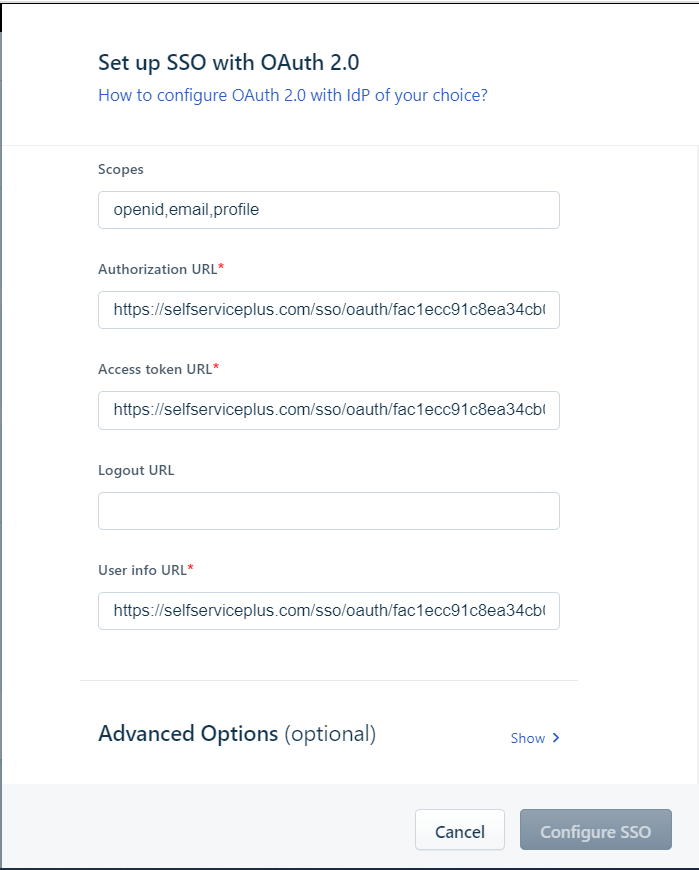
- Copy the Redirect URL, under Map information in IdP, for later steps.
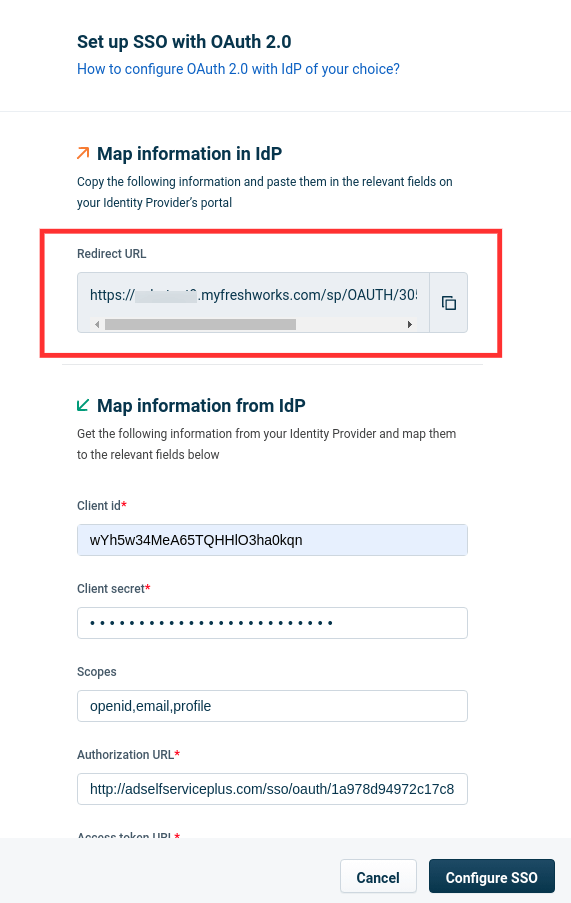
- Click Configure SSO.
ADSelfService Plus (identity provider) configuration steps
- Switch back to ADSelfService Plus' Freshdesk configuration page.
- Enter the Application Name and Description as per your preference.
- Enter the Domain Name of your Freshdesk account. For example, if your Freshdesk username is johnwatts@thinktodaytech.com, then thinktodaytech.com is your domain name.
- Select policies from the Assign policies dropdown, to decide for whom this setting will be applicable.
- Check the box next to Enable OAuth/OpenID Connect in OAuth/OpenID Connect tab.
- Enter the Redirect URL copied in step 9 of Freshdesk configuration in the Login Redirect URL field.
- Scopes specify the level of access the access token has. The scopes are generally provided in the authorization request so, you don't have to specify them here. If the scopes are not mentioned by your service provider, you must add them in this field.
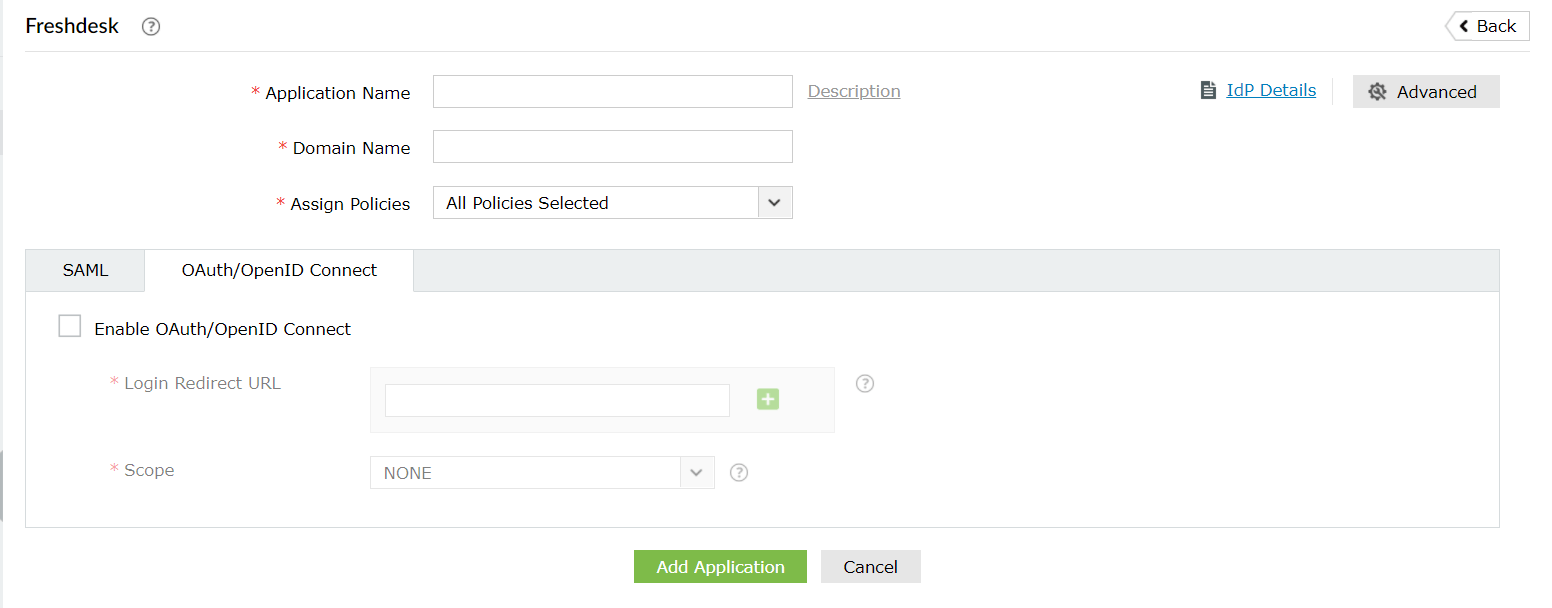
- Click Add Application to save these settings.
- The Well-known Configuration URL in IdP details pop-up contains all the endpoint values, supported scopes, response modes, client authentication modes and client details. This is enabled only after you save the application in ADSelfService Plus. You can provide this to your service provider if required.









