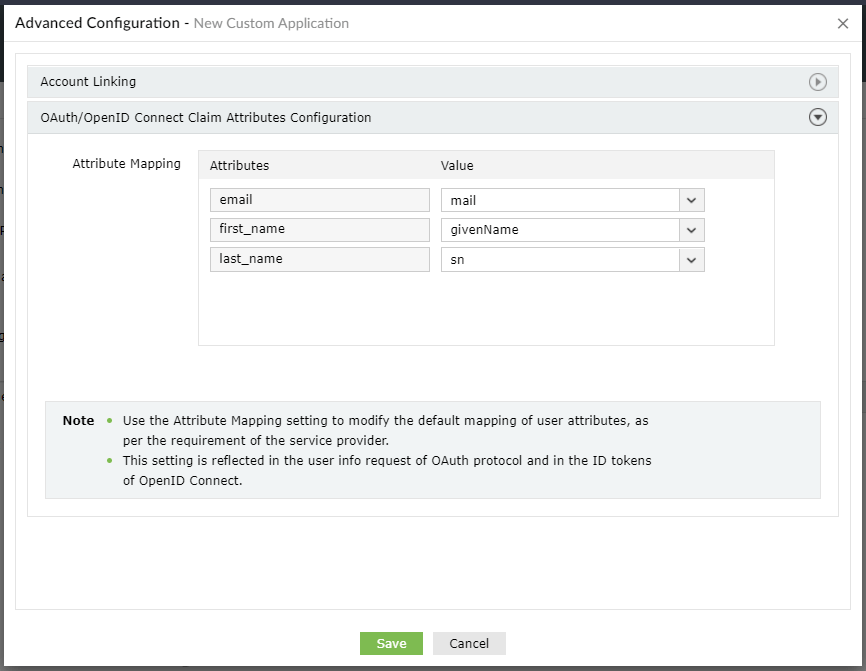
ADSelfService Plus supports SSO configuration to any OAuth/OpenID Connect-enabled custom enterprise application. In this page, we discuss the steps to configure OpenID Connect-based SSO for custom applications.
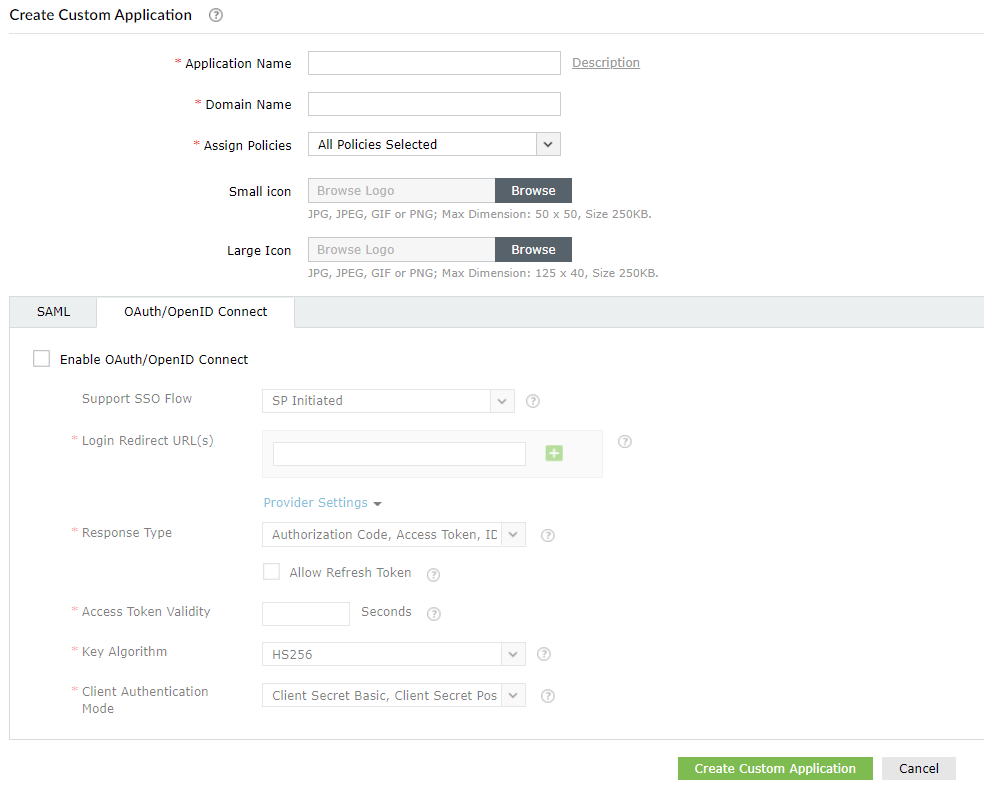
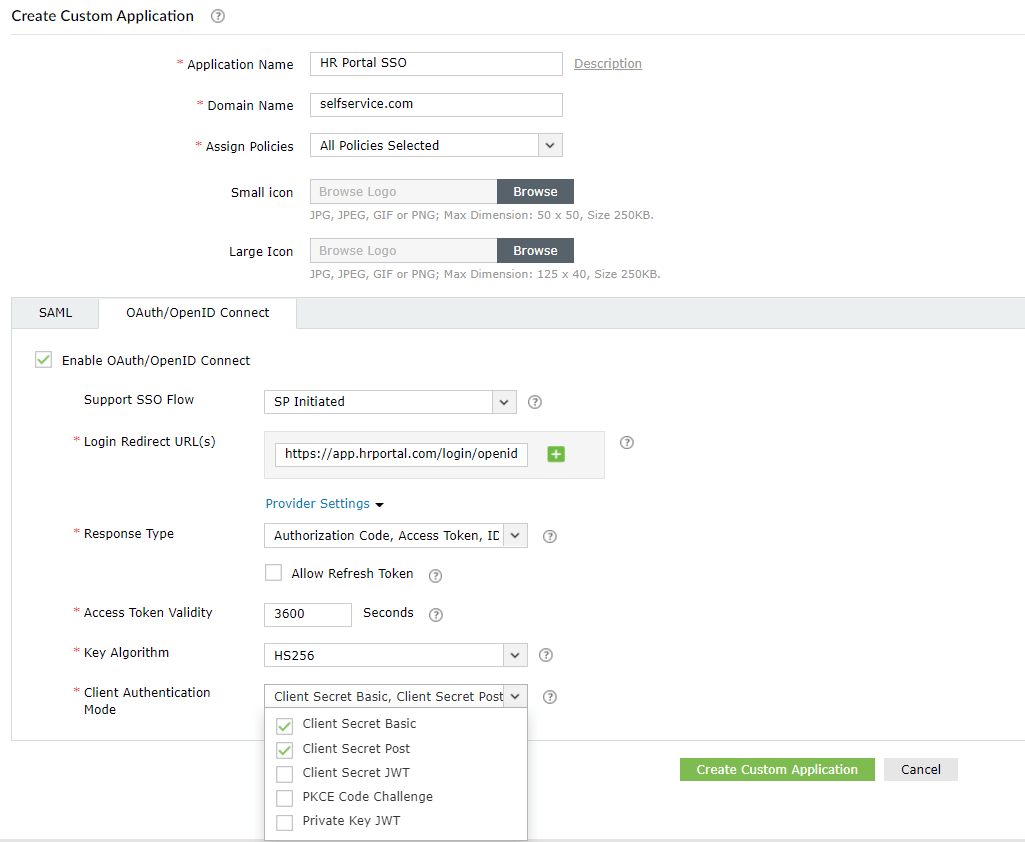
In the Login Redirect URL(s) field, enter all the available Authorization redirect or callback URL(s) obtained from your Service Provider in step 2 of pre-requisites. The URL(s) can be found in the Service Provider's OAuth/OIDC SSO configuration page.
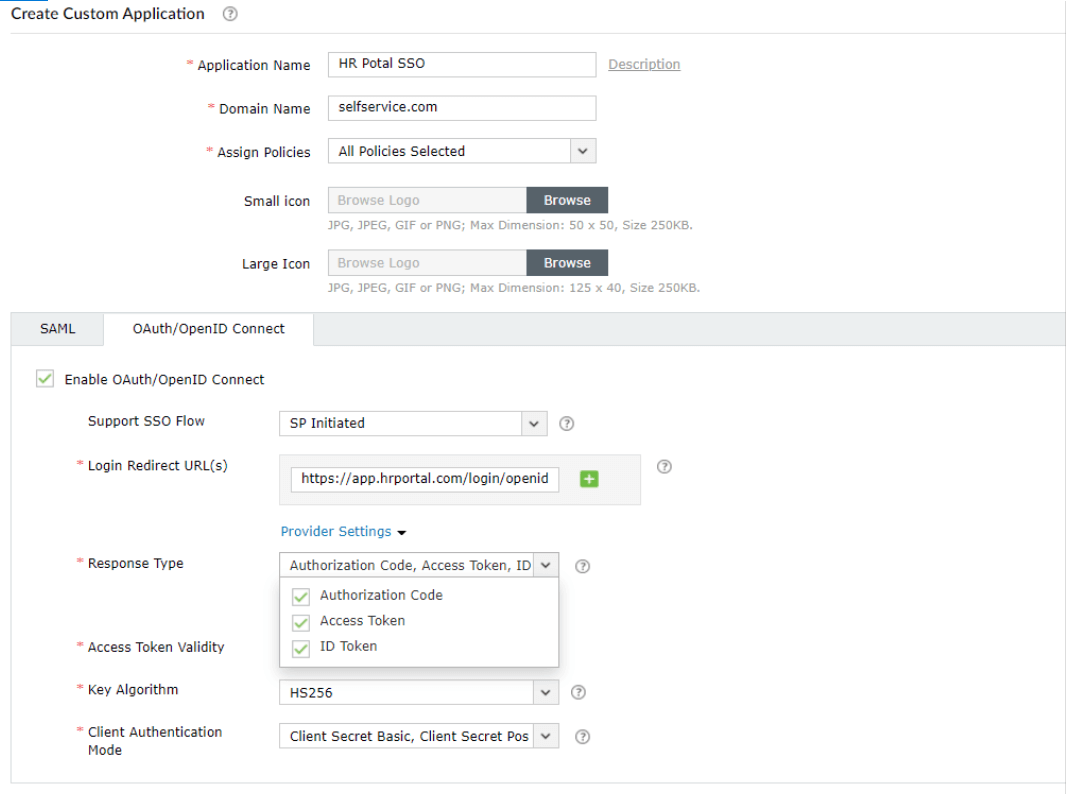
The IdP Login Initiate URL, is used to send id_token from Identity Provider to Service Provider. Once this URL is configured, the users will be able to log in to the Service Provider by clicking on that particular application in the Applications tab in ADSelfService Plus.
In the Login Redirect URL(s) field, enter all the available Authorization redirect or callback URL(s) obtained from your Service Provider in step 2 of pre-requisites. The URL(s) can be found in the Service Provider's OAuth/OIDC SSO configuration page.
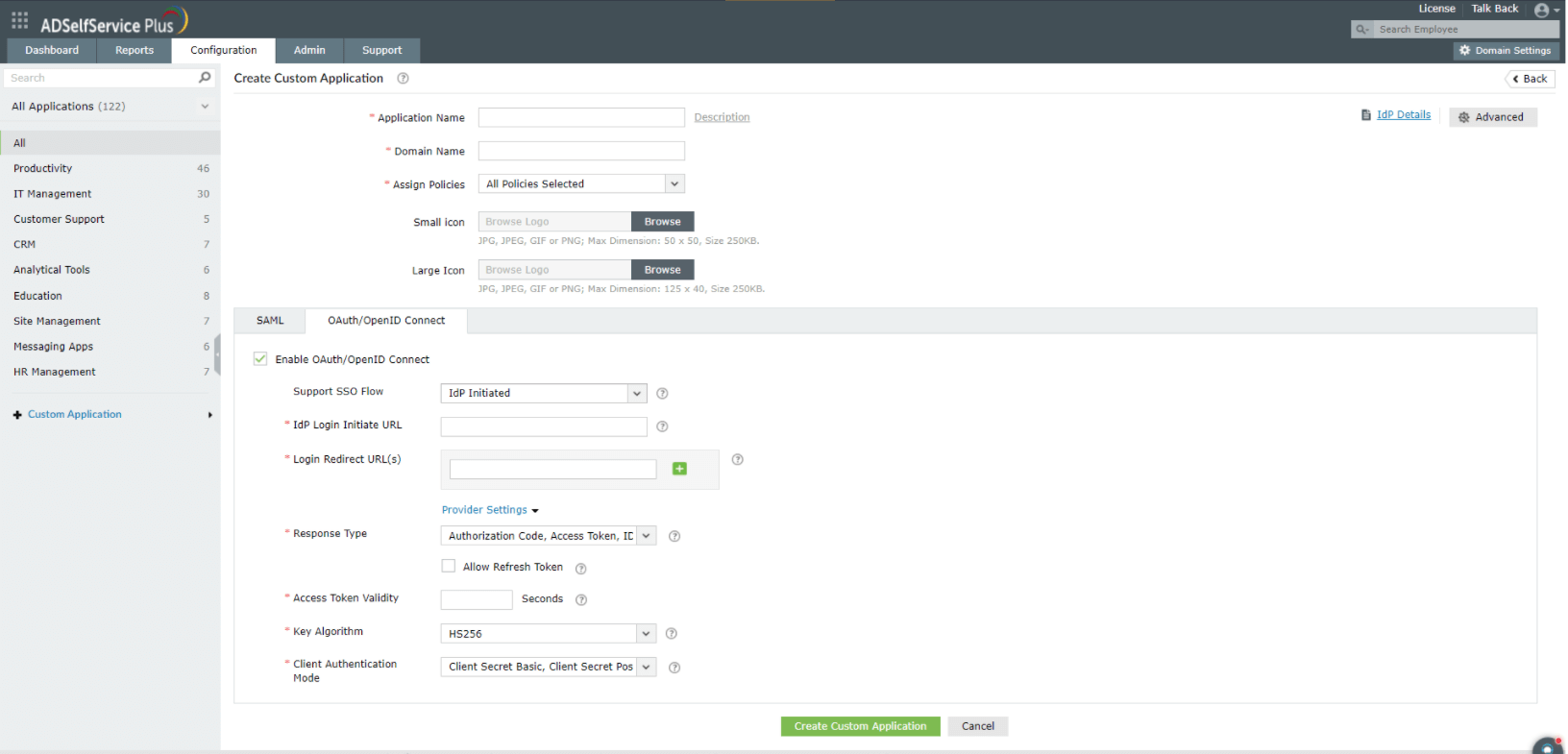
HS256 - A symmetric algorithm that uses one shared secret (i.e. client_secret generated during custom application creation in IdP), to sign and validate the token instead of using a public key pair.
RS256 - RSA signature with SHA-256. It is an asymmetric algorithm which uses a public or private key pair, generated and managed by IdP (the IdP uses the private key to generate the signature, and the application uses a public key to validate the signature).
RS384 - Same as RS256. Only difference is this uses a SHA-384 hashing algorithm for creating the RSA signature.
RS512 - Same as RS256. Only difference is this uses a SHA-512 hashing algorithm for creating the RSA signature.
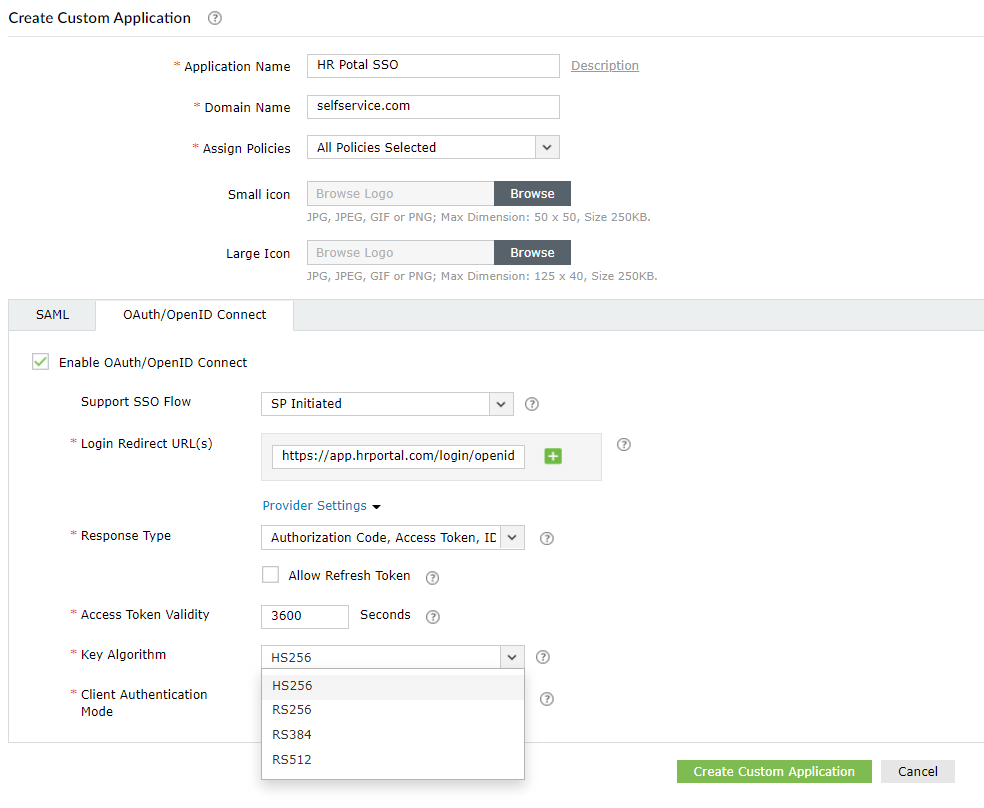
Client Secret Basic: The IdP generates a client_id and client_secret and shares it with the Service Provider in advance. While sending access token request, the Service Provider, encodes the client_id and client_secret in BASE64 and sets it in the authorization header. The IdP verifies this authorization header to authorize the request.
Client Secret Post: The IdP generates a client_id and client_secret and shares it with the Service Provider in advance. While sending access token request, the Service Provider, sets the client_id and client_secret in the access token request body. The IdP verifies the client_id and client_secret in the request body to authorize the request.
PKCE Code Challenge: In this authentication method, the Service Provider generates a random value called code_verifier, which is hashed to form a code_challenge. While sending access token request, the Service Provider sends this code_challenge to the IdP. The IdP checks this code_challenge to authorize the request.
Client Secret JWT: The IdP generates a client secret (client_secret_jwt) and shares it with the Service Provider in advance. While sending access token request, the Service Provider, uses this secret to generate a digital signature. The IdP checks for the signature to authorize the request.
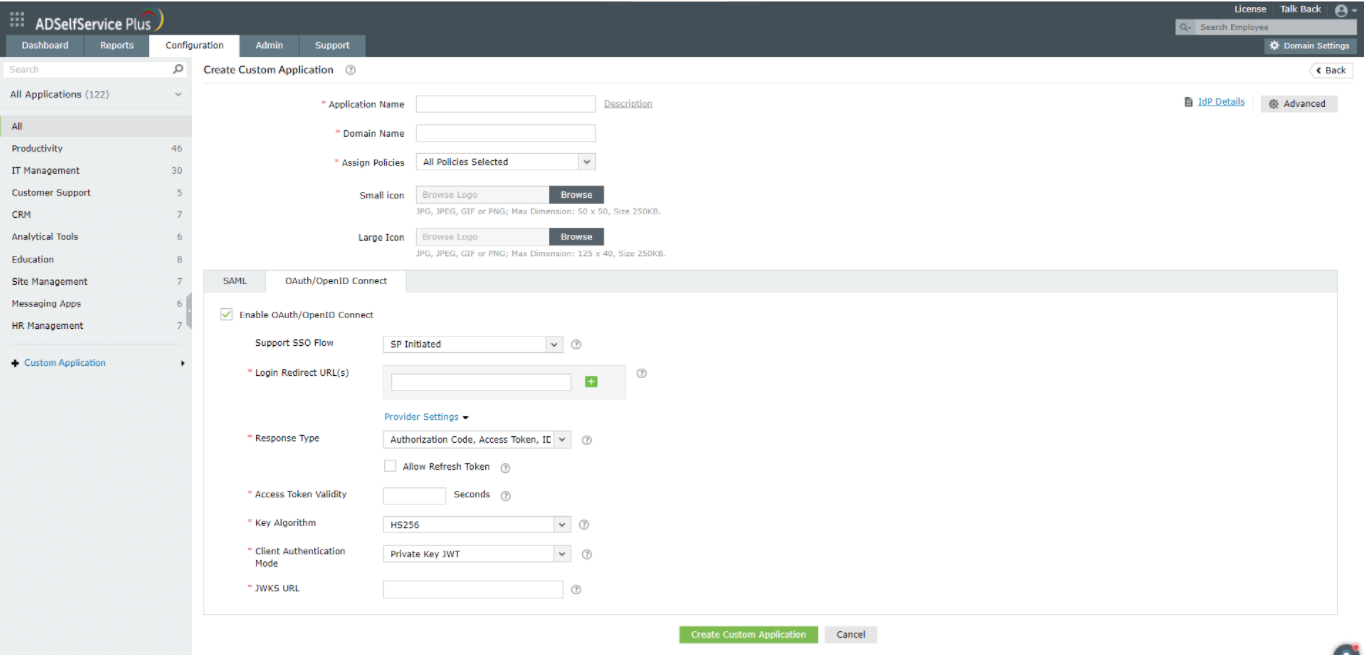
Private Key JWT: The IdP gets a JWKS URL (JSON web key set) from the Service Provider that consists of a public key. While sending access token request, the Service Provider, uses a private key to generate a digital signature. The IdP checks for the signature using the public key obtained from JWKS URL, to authorize the request.
Copyright © 2023, ZOHO Corp. All Rights Reserved.